This internship report is an exclusive study of the works in the department of LAN system & Security Solution in china-Bangla Group. The main purpose of this report is to get the practical experience through observing the system operations works at China-Bangla Group.
These three months of internship at China-Bangla has helped me a lot to understand about the practical working environment in a networking system. This report describes backbone LAN along with the implementation; infrastructure and functioning of the various network elements in general. The report also focused on the works of the intelligent Network. Thus my report will be combination of different aspects of the client deals and operations under general working activities and a comprehensive view IT division. An effort has been made to identify some problems and prospects and to provide recommendation for solving those problems as an intern. I will be describing my duties, activities and knowledge gained from the experiences.
All the observation which is made through the internee period that has been reflected in this report which proper analysis based on theory and practical experience.
Objectives
The objective of this internship was to gain experience and knowledge regarding the existing cellular services and to co-relate the theoretical background learned university courses with the practical working environment. In the field of engineering, concepts at application level provide a useful supplement to relevant theories and understandings. This program also bring out more information of official decorum and also fulfill the academic requirement for the under graduate program. Internship gives us the opportunity to learn how to cope up with the real corporate world and also to learn the teamwork.
Report objective
The objective of this report is to represent the experience and outcomes gathered during the internship in a formal context. This report discusses for the fact that this writer performed his internship in the Regional Operation Division of China-Bangla Group. The report is arranged in chapters which are laid out in a manner so that the report provides the reader with sufficient background information of works of all the wings of system operation and for the understanding of rather advanced discussions and further discussions along with the supporting figures are also given at places so that they complement the text and aid its understanding.
Company Profile
China-Bangla Group. Is a Real Estate Company, started with a few land in INANI at the world famous longest and unbroken Sea beach in Cox’s Bazar.Bying a land in a good location is the best decision you make in your life and to avoid any problem and risk with buying lands we are the right person in the right time. We are looking for that hardworking person who is really working for the tourist in different standard hotels with small salary and having a dream of making hotel after a certain time in their life. For it’s easy to buy a land of 1 biga or more to build up a project of tourist entertainment.
Your small investment today will be smart returns in the near future.
Introduction to WLAN
Despite the productivity, convenience and cost advantage that WLAN offers, the radio waves used in wireless networks create a risk where the network can be hacked. This section explains three examples of important threats: Denial of Service, Spoofing, and Eavesdropping
WLAN Components
In this kind of attack, the intruder floods the network with either valid or Invalid messages affecting the availability of the network resources. Due to the nature of the radio transmission, the WLAN are very vulnerable Against denial of service attacks. The relatively low bit rates of WLAN can easily be overwhelmed and leave them open to denial of service attacks . by using a powerful enough transceiver, radio interference can easily Be generated that would unable WLAN to communicate using radio path
Access Points
Access Point (AP) is essentially the wireless equivalent of a LAN hub. It is typically connected with the wired backbone through a standard Ethernet Cable, and communicates with wireless devices by means of an antenna. An AP operates within a specific frequency spectrum and uses 802.11 standard specified modulation techniques. It also informs the wireless Clients of its availability, and authenticates and associates wireless clients to the wireless network.
Network Interface Cards (Nicks)/client adapters
Wireless client adapters connect PC or workstation to a wireless network either in ad hoc peer-to-peer mode or in infrastructure mode with Apes (will be discussed in the following section). Available in PCMCIA (Personal Computer Memory Card international Association) card and PCI (Peripheral Component Interconnect), it connects desktop and mobile computing devices wirelessly to all network resources. The NIC scans the Available frequency spectrum for connectivity and associates it to an access point or another wireless client. It is coupled to the PC/workstation operating system using a software driver. The NIC enables new employees to be connected instantly to the network and enable Internet access in conference rooms.
WLAN Architecture
The WLAN components mentioned above are connected in certain Configurations. There are three main types of WLAN architecture: Independent, Infrastructure, and Micro cells and Roaming.
Independent WLAN
The simplest WLAN configuration is an independent (or peer-to-peer)
WLAN. It is a group of computers, each equipped with one wireless LAN NIC/client adapter. In this type of configuration, no access point is necessary and each computer in the LAN is configured at the same radio channel to enable peer-to-peer networking. Independent networks can be set up whenever two or more wireless adapters are within range of each other. Figure 1 shows the architecture of Independent WLAN.
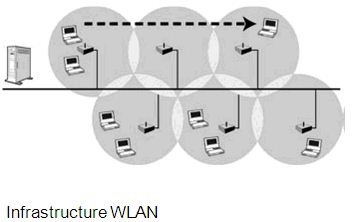
Infrastructure WLAN
Infrastructure WLAN consists of wireless stations and access points. Access Points combined with a distribution system (such as Ethernet) support the creation of multiple radio cells that enable roaming throughout a facility. The access points not only provide communications with the wired network but also mediate wireless network traffic in the immediate neighborhood. This network configuration satisfies the need of large-scale networks arbitrary coverage size and complexities. Figure 2 shows the architecture of Infrastructure WLAN
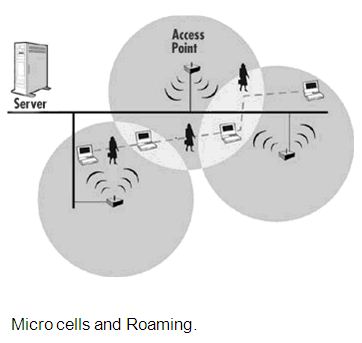
Micro cells and Roaming
The area of coverage for an access point is called a “micro cell’. The installation of multiple access points is required in order to extend the WLAN range beyond the coverage of a single access. One of the main benefits of WLAN is user mobility. Therefore, it is very important to ensure that users can move seamlessly between access points without having to log in again and restart their applications. Seamless roaming is only possible if the access points have a way of exchanging information as abuser connection is handed off from one access point to another. In a setting with overlapping micro cells, wireless nodes and access points frequently check the strength and quality of transmission. The WLAN system hands off roaming users to the access point with the strongest and highest quality signal, in accommodating roaming from one micro cell to another. Figure 3 shows the architecture of Micro cells and Roaming.
Security Threats of WLAN
Despite the productivity, convenience and cost advantage that WLAN offers, the Radio waves used in wireless networks create a risk where the network can be hacked. This section explains three examples of important threats: Denial of Service, Spoofing, and Eavesdropping.
Denial of Service
In this kind of attack, the intruder floods the network with either valid or invalid messages affecting the availability of the network resources. Due to the nature of the radio transmission, the WLAN are very vulnerable against denial of service attacks. The relatively low bit rates of WLAN can easily be overwhelmed and leave them open to denial of service attacks. By using a powerful enough transceiver, radio interference can easily Be generated that would unable WLAN to communicate using radio path.
Spoofing and Session Hijacking
This is where the attacker could gain access to privileged data and Resources in the network by assuming the identity of a valid user. This happens because 802.11 networks do not authenticate the source Address, which is Medium Access Control (MAC) address of the frames. Attackers may therefore spoof MAC addresses and hijack sessions. Moreover, 802.11 do not require an Access Point to prove it is actually an AP. This facilitates attackers who may masquerade as AP’s. In eliminating spoofing, proper authentication and access control mechanisms need to be placed in the WLAN.
Eavesdropping
This involves attack against the confidentiality of the data that is being transmitted across the network. By their nature, wireless LANs intentionally radiates network traffic into space. This makes it impossible to control who can receive the signals in any wireless LAN installation. In the wireless network, eavesdropping by the third parties is the most significant threat because the attacker can intercept the transmission over the air from a distance, away from the premise of the company.
Wired Equivalent Privacy
Wired Equivalent Privacy (WEP) is a standard encryption for wireless networking. It is a user authentication and data encryption system from IEEE 802.11 used to overcome the security threats. Basically, WEP provides security to WLAN by encrypting the information transmitted over the air, so that only the receivers who have the correct encryption key can decrypt the information. The following section explains the technical functionality of WEP as the main security protocol for WLAN.
How WEP Works?
When deploying WLAN, it is important to understand the ability of WEP to Improve security. This section describes how WEP functions accomplish the level of privacy as in a wired LAN. WEP uses a pre-established shared secret key called the base key, the RC4 encryption algorithm and the CRC-32 (Cyclic Redundancy Code) checksum algorithm as its basic building blocks. WEP supports up to four different base keys, identified by Keyed 0 thorough 3. Each of these base keys is a group key called a default key, meaning that the base keys are shared among all the members of a particular wireless network. Some implementations also support a set of nameless per-link keys called key-mapping keys. However, this is less common in first generation products, because it implies the existence of a key management facility, which WEP does not define. The WEP pacification does not permit the use of both key-mapping keys and default keys simultaneously, and most deployments share a single default key across all of the 802.11 devices. WEP tries to achieve its security goal in a very simple way. It operates on MAC Protocol Data Units (Medusa), the 802.11 packet fragments. To protect the data in an MPDU, WEP first computes an integrity check value (ICV) over to the MPDU data. This is the CRC-32 of the data. WEP appends the ICV to the end of the data, growing this field by four bytes. The ICV allows the receiver to detect if data has been corrupted in flight or the packet is an outright forgery. Next, WEP selects a base key and an initialization vector (IV), which is a 24-bit value. WEP constructs a per-packet RC4 key by concatenating the IV value and the selected shared base key. WEP then uses the per-packet key to RC4, and encrypt both the data and the ICV. The IV and Keyed identifying the selected key are encoded as a four-byte string and pre-pended to the encrypted data.
How to Use WEP Parameters:
WEP data encryption is used when the wireless devices are configured to operate in Shared Key authentication mode. There are two shared key methods implemented in most commercially available products, 64-bit and 128-bit WEP data encryption. Before enabling WEP on an 802.11 network, you must first consider what type of encryption you require and the key size you want to use. Typically, there are three WEP Encryption options available for 802.11 products:
• Do Not Use WEP: The 802.11 network does not encrypt data. For authentication purposes, the network uses Open System Authentication.
• Use WEP for Encryption: A transmitting 802.11 device encrypts the data portion of every packet it sends using a configured WEP key. The receiving 802.11g device decrypts the data using the same WEP key. For authentication purposes, the 802.11g network uses Open System Authentication.
• Use WEP for Authentication and Encryption: A transmitting 802.11 device encrypts the data portion of every packet it sends using a configured WEP key. The receiving 802.11 device decrypts the data using the same WEP key. For authentication purposes, the 802.11 network uses Shared Key Authentication.
The IEEE 802.11 standard defines the WEP base key size as consisting of 40 Bits, so the per-packet key consists of 64 bits once it is combined with the IV. Many in the 802.11 community once believed that small key size was a security problem, so some vendors modified their products to support a 104-bit base key as well. This difference in key length does not make any different in the overall security. An attacker can compromise its privacy goals with comparable effort regardless of the key size used. This is due to the vulnerability of the WEP construction which will be discussed in the next section.
WEP Authentication
The 802.11 standard defines several services that govern how two 802.11 devices communicate. The following events must occur before an 802.11 station can communicate with an Ethernet network through an access point such as the one built in to the NETGEAR product: . Turn on the wireless station. . The station listens for messages from any access points that are in range. . The station finds a message from an access point that has a matching SSID. . The station sends an authentication request to the access point. . The access point authenticates the station. . The station sends an association request to the access point. . The access point associates with the station. 8. The station can now communicate with the Ethernet network through the access point. An access point must authenticate a station before the station can associate with the access point or communicate with the network. The IEEE 802.11 standard defines two types of WEP authentication: Open System and Shared Key. • Open System Authentication allows any device to join the network, assuming that the device SSID matches the access point SSID. Alternatively, the device can use the “ANY” SSID option to associate with any available access point within range, regardless of its SSID.
WPA Wireless Security
Wi-Fi Protected Access (WPA) is a specification of standards-based, interoperable security enhancements that increase the level of data protection and access control for existing and future wireless LAN systems. The IEEE introduced the WEP as an optional security measure to secure 802.11g (Wi-Fi) WLANs, but inherent weaknesses in the standard soon became obvious. In response to this situation, the Wi-Fi Alliance announced a new security architecture in October 2002 that remedies the shortcomings of WEP. This standard, formerly known as Safe Secure Network (SSN), is designed to work with existing 802.11 products and offers forward compatibility with 802.11i, the new wireless security architecture being defined in the IEEE. WPA offers the following benefit.
• Enhanced data privacy • Robust key management • Data origin authentication • Data integrity protection Starting in August of 2003, all new Wi-Fi certified products had to support WPA, and all existing Wi-Fi certified products had one year to comply with the new standard or lose their Wi-Fi certification. NETGEAR has implemented WPA on client and access point products. As of August 2004, all Wi-Fi certified products must support WPA.
What are the Key Features of WPA Security?
The following security features are included in the WPA standard: • WPA Authentication • WPA Encryption Key Management – Temporal Key Integrity Protocol (TKIP) – Michael message integrity code (MIC) – AES Support • Support for a Mixture of WPA and WEP Wireless Clients These features are discussed below. WPA addresses most of the known WEP vulnerabilities and is primarily intended for wireless infrastructure networks as found in the enterprise. This infrastructure includes stations, access points, and authentication servers (typically Remote Authentication Dial-In User Service servers, called RADIUS servers). The RADIUS server holds (or has access to) user credentials (for example, user names and passwords) and authenticates wireless users before they gain access to the network. The strength of WPA comes from an integrated sequence of operations that encompass 802.1X/ EAP authentication and sophisticated key management and encryption techniques. Its major operations include:
• Network security capability determination. This occurs at the 802.11 level and is communicated through WPA information elements in Beacon, Probe Response, and (Re) Association Requests. Information in these elements includes the authentication method (802.1X or Pre-shared key) and the preferred cipher suite (WEP, TKIP, or AES, which is Advanced Encryption Standard). The primary information conveyed in the Beacon frames is the authentication method and the cipher suite. Possible authentication methods include 802.1X and Pre-shared key. Pre-shared key is an authentication method that uses a statically configured passphrase on both the stations and the access point. This removes the need for an authentication server, which in many home and small office environments is neither available nor desirable. Possible cipher suites include: WEP, TKIP, and AES. We say more about TKIP and AES when addressing data privacy below.
• Authentication. EAP over 802.1X is used for authentication. Mutual authentication is gained by choosing an EAP type supporting this feature and is required by WPA. The 802.1X port access control prevents full access to the network until authentication completes. The 802.1X EAPOL-Key packets are used by WPA to distribute per-session keys to those stations successfully authenticated.
Weaknesses of WEP
WEP has undergone much scrutiny and criticism that it may be compromised.
What makes WEP vulnerable? The major WEP flaws can be summarized into
Three categories.
No forgery protection
There is no forgery protection provided by WEP. Even without knowing the
Encryption key, an adversary can change 802.11 packets in arbitrary, undetectable ways, deliver data to unauthorized parties, and masquerade as an authorized user. Even worse, an adversary can also learn more about the encryption key with forgery attacks than with strictly passive attacks.
No protection against replays
WEP does not offer any protection again replays. An adversary can create
Forgeries without changing any data in an existing packet, simply by recording WEP packets and then retransmitting later. Replay, a special type of forgery attack, can be used to derive information about the encryption key and the data it protects.
Reusing initialization vectors
By reusing initialization vectors, WEP enables an attacker to decrypt the Encrypted data without the need to learn the encryption key or even resorting to high-tech techniques. While often dismissed as too slow, a patient attacker can compromise the encryption of an entire network after only a few reports done by a team at the University of California’s computer science department presented the insecurity of WEP which expose WLAN to several types of security breaches. The ISAAC (Internet Security, Applications, Authentication and Cryptography) team which released the report quantifies two types of weaknesses in WEP. The first weakness emphasizes on limitations of the initialization Vector (IV). The value of the IV often depends on how vendor
Chose to implement it because the original 802.11 protocol did not specify how this value is derived. The second weakness concerns on RC4’s Integrity Check Value (ICV), a CRC-32 checksum that is used to verify whether the contents of a frame have been modified in transit. At the time of encryption, this value is added to the end of the frame. As the recipient decrypts the packet, the checksum is used to validate the data. Because the ICV is not encrypted, however, it is theoretically possible to change the data payload as long as you can derive the appropriate bits to change in the ICV as well. This means data can be tampered and falsified.
Practical Solutions for Securing WLAN
Service Set Identifier (SSID) is a unique identifier attached to the header of packets sent over a WLAN that acts as a password when a mobile device tries to connect to a particular WLAN. The SSID differentiates one WLAN from another, so all access points and all devices attempting to connect to a specific WLAN must use the same SSID. In fact, it is the only security mechanism that the access point requires to enable association in the absence of activating optional security features. Not changing the default SSID is one of the most common security mistakes made by WLAN administrators. This is equivalent to leaving a default password in place.
Changing Default SSID
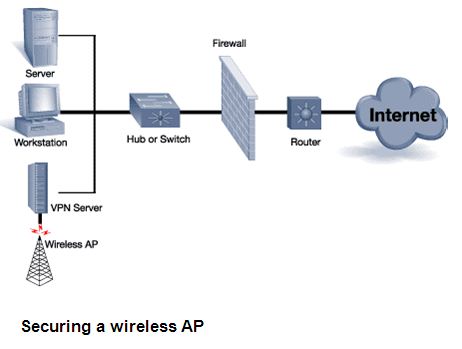
A VPN is a much more comprehensive solution in a way that it authenticates users coming from an entrusted space and encrypts their communication so that someone listening cannot intercept it. Wireless AP is placed behind the corporate firewall within a typical wireless implementation. This type of implementation opens up a big hole within the trusted network space. A secure method of implementing a wireless AP is to place it behind a VPN server. This type of implementation provides high security for the wireless network implementation without adding significant overhead to the users. If there is more than one wireless AP in the organization, it is recommended to run them all into a common switch, then connecting the VPN server to the same switch. Then, the desktop users will not need to have multiple VPN dial-up connections configured on their desktops. They will always be authenticating to the same VPN server no matter which wireless AP they have associated with. Figure 5 shows secure method of implementing a wireless AP.
Utilize Static IP
By default, most wireless LANs utilize DHCP (Dynamic Host Configuration
Protocol) to more efficiently assign IP addresses automatically to user devices. A problem is that DHCP does not differentiate a legitimate user from a hacker. With a proper SSID, anyone implementing DHCP will obtain an IP address automatically and become a genuine node on the network. By disabling DHCP and assigning static IP addresses to all wireless users, you can minimize the possibility of the hacker obtaining a valid IP address. This limits their ability to access network services. On the other hand, someone can use an 802.11 packet analyzer to sniff the exchange of frames over the network and learn what IP addresses are in use. This helps the intruder in guessing what IP address to use that falls within the range of ones in use. Thus, the use of static IP addresses is not fool proof, but at least it is a deterrent. Also keep in mind that the use of static IP addresses in larger networks is very cumbersome, which may prompt network managers to use DHCP to avoid support issues.
Access Point Placement
WLAN access points should be placed outside the firewall to protect intruders from accessing corporate network resources. Firewall can be configured to enable access only by legitimate users based on MAC and IP addresses. However, this is by no means a final or perfect solution Because MAC and IP addresses can be spoofed even though this makes it difficult for a hacker to mimic.
Minimize radio wave propagation in non-user areas
Try orienting antennas to avoid covering areas outside the physically Controlled boundaries of the facility. By steering clear of public areas, such as parking lots, lobbies, and adjacent offices, the ability for an intruder to participate on the wireless LAN can be significantly reduced. This will also minimize the impact of someone disabling the wireless LAN with jamming Techniques.
LAN Security:
Hubs & Switches
LAN equipment, hubs, bridges, repeaters, routers, switches will be kept in secure hub rooms. Hub rooms will be kept locked at all times. Access to hub rooms will be restricted to I.T. Department staff only. Other staff, and contractors requiring access to hub rooms will notify the I.T. Department in advance so that the necessary supervision can be arranged.
Workstations
Users must logout of their workstations when they leave their workstation for any length of time. Alternatively Windows workstations may be locked.
. All unused workstations must be switched off outside working hours.
Wiring
All network wiring will be fully documented.
All unused network points will be de-activated when not in use.
All network cables will be periodically scanned and readings recorded for future reference.
Users must not place or store any item on top of network cabling.
. Redundant cabling schemes will be used where possible.
Monitoring Software
The use of LAN analyzer and packet sniffing software is restricted to the I.T. Department.
LAN analyzers and packet snuffers will be securely locked up when not in use.
Intrusion detection systems will implemented to detect unauthorized access to the network
Servers
All servers will be kept securely under lock and key.
Access to the system console and server disk/tape drives will be restricted to authorized I.T. Department staff only.
Electrical Security
All servers will be fitted with Puss’s that also condition the power supply.
All hubs, bridges, repeaters, routers, switches and other critical network equipment will also be fitted with Puss’s.
In the event of a mains power failure, the Puss’s will have sufficient power to keep the network and servers running until the generator takes over.
Software will be installed on all servers to implement an orderly shutdown in the event of a total power failure.
All Puss’s will be tested periodically.
Inventory Management
The I.T. Department will keep a full inventory of all computer equipment and software in use throughout the Company.
Computer hardware and software audits will be carried out periodically via the use of a desktop inventory package. These audits will be used to track unauthorized copies of software and unauthorized changes to hardware and software configurations
New Standards for Improving WLAN Security
Apart from all of the actions in minimizing attacks to WLAN mentioned in the
Previous section, we will also look at some new standards that intend to improve the security of WLAN. There are two important standards that will be discussed in this paper: 802.1x and 802.11i.
802.1x
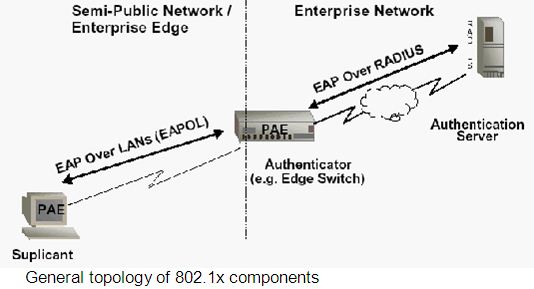
One of the standards is 802.1 as which was originally designed for wired Ethernet networks. This standard is also part of the 802.11i standard that will be discussed later. The following discussion of 802.1 as is divided into three parts, starting with the concept of Point-to-Point Protocol (PPP), followed by Extensible Authentication Protocol (EAP), and continues with the understanding of 802.1x itself. IEEE 802.1x relates to EAP in a way that it is a standard for carrying EAP Over a wired LAN or WLAN. There are four important entities that explain This standard.
PPP
The Point-to-Point Protocol (PPP) originally emerged as an encapsulation
Protocol for transporting IP traffic over point-to-point links. PPP also established a standard for the assignment and management of IP addresses, asynchronous (start/stop) and bit-oriented synchronous encapsulation, network protocol multiplexing, link configuration, link quality testing, error detection, and option negotiation for such capabilities as network-layer address negotiation and data-compression negotiation By any measure, PPP is a good protocol. However, as PPP usage grew, people quickly found its limitation in terms of security. Most corporate networks want to do more than simple usernames and passwords for secure access . This leads to the designation of a new authentication protocol, called Extensible Authentication Protocol (EAP).
EAP
The Extensible Authentication Protocol (EAP) is a general authentication protocol defined in IETF (Internet Engineering Task Force) standards. It was originally developed for use with PPP. It is an authentication protocol that provides a generalized framework for several authentication mechanisms [15]. These include Kerberos, public key, smart cards and one-time passwords. With a standardized EAP, interoperability and compatibility across authentication methods become simpler. For example, when user dials a remote access server (RAS) and use EAP as part of the PPP connection, the RAS does not need to know any of the details about the authentication system. Only the user and the authentication server have to be coordinated. By supporting EAP authentication, RAS server does not actively participate in the authentication dialog. Instead, RAS just re-packages EAP packets to hand Off to a RADIUS server to make the actual authentication decision. How does EAP relate to 802.1 xs? The next section will explain the relation.
I Authenticator
Authenticator is the entity that requires the entity on the other end of the link to be authenticated. An example is wireless access Points.
ii. Supplicant
Supplicant is the entity being authenticated by the Authenticator And desiring access to the services of the Authenticator.
iii. Port Access Entity (PAE)
It is the protocol entity associated with a port. It may support the Functionality of Authenticator, Supplicant or both.
iv. Authentication Server
Authentication server is an entity that provides authentication Service to the Authenticator. It maybe co-located with Authenticator, But it is most likely an external server. It is typically a RADIUS (Remote Access Dial in User Service) server. The supplicant and authentication server are the major parts of 802.1 as
EAP messages are encapsulated in Ethernet LAN packets (EAPOL) to Allow communications between the supplicant and the authenticator. The Following are the most common modes of operation in EAPOL.
I. The authenticator sends an “EAP-Request/Identity” packet to the supplicant as soon as it detects that the link is active.
ii. Then, the supplicant sends an “EAP-Response/Identity” Packet to the authenticator, which is then passed to the Authentication (RADIUS) server.
iii. Next, the authentication server sends back a challenge to the authenticator, with a token password system. The authenticator unpacks this from IP and repackages it into EAPOL and sends it to the supplicant. Different authentication methods will vary this message and the total number of messages. EAP supports client-only authentication and strong mutual authentication. Only strong mutual authentication is considered appropriate for the wireless case.
802.11i
In addition to 802.1x standard created by IEEE, one up-and-coming 802.11x specification, which is 802.11i, provides replacement technology for WEP security. 802.11i is still in the development and approval processes. In this paper, the key technical elements that have been defined by the specification will be discussed. While these elements might change, the information provided will provide insight into some of the changes that 802.11i promises to deliver to enhance the security features provided in a WLAN system.
The 802.11i specification consists of three main pieces organized into two layers. On the upper layer is the 802.1x, which has been discussed in the previous section. As used in 802.11i, 802.1 xs provides a framework for robust user authentication and encryption key distribution. On the lower layer are improved encryption algorithms. The encryption algorithms are in the form of the TKIP (Temporal Key Integrity Protocol) and the CCMP (counter mode with CBC-MAC protocol). It is important to understand how all of these three ices work to form the security mechanisms of 802.11i standard. Since the concept of 802.1 xs has been discussed in the previous section, the following section of this paper will only look at TKIP and CCMP. Both of these encryption protocols provide Enhanced data integrity over WEP, with TKIP being targeted at legacy Equipment, while CCMP is being targeted at future WLAN equipments. However A true 802.11i system uses either the TKIP or CCMP protocol for all equipments. WPA is forward-compatible with the IEEE 802.11i security specification currently under development. WPA is a subset of the current 802.11i draft and uses certain pieces of the 802.11i draft that were ready to bring to market in 2003, such as 802.1x and TKIP. The main pieces of the 802.11i draft that are not included in WPA are secure IBSS (Ad-Hoc mode), secure fast handoff (for specialized 802.11 VoIP phones), as well as enhanced encryption protocols such as AES-CCMP. These features are either not yet ready for market or will require hardware upgrades to implement.
WEP Wireless Security The absence of a physical connection between nodes makes the wireless links vulnerable to eavesdropping and information theft. To provide a certain level of security, the IEEE 802.11 standard has defined two types of authentication methods, Open System and Shared Key. With Open System authentication, a wireless computer can join any network and receive any messages that are not encrypted. With Shared Key authentication, only those computers that possess the correct authentication key can join the network. By default, IEEE 802.11 wireless devices operate in an Open System network. Recently, Wife, the Wireless Ethernet Compatibility Alliance developed the Wi-Fi Protected Access (WPA), a new strongly enhanced Wi- Fi security. WPA will soon be incorporated into the IEEE 802.11 standard.
TKIP
The temporal key integrity protocol (TKIP) which initially referred to as WEP2, was signed to address all the known attacks and deficiencies in the WEP algorithm. According to 802.11 Planet [6], the TKIP security process begins with a 128-bit temporal-key, which is shared among clients and access points. TKIP combines the temporal key with the client machine’s MAC address and then adds a relatively large 16-octet initialization vector to produce the key that will encrypt the data. Similar to WEP, TKIP also uses RC4 to perform the encryption. However, TKIP Changes temporal key every 10,000 packets. This difference provides a dynamic distribution method that significantly enhances the security of the network. TKIP is weaknesses in WEP security, especially the reuse of encryption keys. The following are four new algorithms and their function that TKIP adds to WEP
I. A cryptographic message integrity code, or MIC, called Michael, to defeat forgeries. ii. A new IV sequencing discipline, to remove replay attacks from the attacker’s arsenal. iii. A per-packet key mixing function, to de-correlate the public IVs from weak keys. iv. A re-keying mechanism, to provide fresh encryption and integrity keys, undoing the threat of attacks stemming from Key reuse.
CCMP
As explained previously, TKIP was designed to address deficiencies in WEP; however, TKIP is not viewed as a long-term solution for WLAN Security. In addition to TKIP encryption, the 802.11i draft defines a new Encryption method based on the advanced encryption standard (AES). The AES algorithm is a symmetric block cipher that can encrypt and Decrypt information. It is capable of using cryptographic keys of 128, 192, And 256 bits to encrypt and decrypt data in blocks of 128 bits . More robust than TKIP, the AES algorithm would replace WEP and RC4. AES based encryption can be used in many different modes or algorithms. The mode that has been chosen for 802.11 is the counter mode with CBCMAC protocol CCMP). The counter mode delivers data privacy while the CBC-MAC delivers data integrity and authentication. Unlike TKIP, CCMP is mandatory for anyone implementing 802.11i.
TCP/IP & Internet Security
. Permanent connections to the Internet will be via the means of a firewall to regulate network traffic.
Permanent connections to other external networks, for offsite processing etc., will be via the means of a firewall to regulate network traffic.
Where firewalls are used, a dual homed firewall (a device with more than one TCP/IP address) will be the preferred solution.
Network equipment will be configured to close inactive sessions.
Where modem pools or remote access servers are used, these will be situated on the DMZ or non-secure network side of the firewall.
Workstation access to the Internet will be via the Organization’s proxy server and website content scanner
All incoming e-mail will be scanned by the Organization’s e-mail content scanner.
Voice System Security
DISA port access (using inbound 0800 numbers) on the PBX will be protected by a secure password.
The maintenance port on the PBX will be protected with a secure password.
The default DISA and maintenance passwords on the PBX will be changed to user defined passwords.
. Call accounting will be used to monitor access to the maintenance port, DISA ports and abnormal call patterns.
DISA ports will be turned off during non working hours.
. Internal and external call forwarding privileges will be separated, to prevent inbound calls being forwarded to an outside line.
The operator will Endeavour to ensure that an outside call is not transferred to an outside line.
Use will be made of multilevel passwords and access authentication where available on the PBX.
Voice mail accounts will use a password with a minimum length of six digits.
The voice mail password should never match the last six digits of the phone number.
. The caller to a voice mail account will be locked out after three attempts at password validation.
Dialing calling party pays numbers will be prevented.
. Telephone bills will be checked carefully to identify any misuse of the telephone system.
Tools for Protecting WLAN
There are some products that can minimize the security threats of WLAN such as:
Air Defense™
It is a commercial wireless LAN intrusion protection and management System that discovers network vulnerabilities, detects and protects a WLAN from intruders and attacks, and assists in the management of a WLAN. Air Defense also has the capability to discover vulnerabilities and Threats in a WLAN such as rogue Apes and ad hoc networks. Apart from Securing a WLAN management functionality that allows users to understand their network, monitor network performance and enforce network policies.
Isomer Wireless Sentry
This product from Isomer Ltd. automatically monitors the air space of the Enterprise continuously using unique and sophisticated analysis technology to identify insecure access points, security threats and wireless network problems. This is a dedicated appliance employing an Intelligent Conveyor Engine (ICE) to passively monitor wireless networks for threats and inform the security managers when these occur. It is a completely automated system, centrally managed, and will integrate seamlessly with existing security infrastructure. No additional man-time is required to Operate the system.
Wireless Security Auditor (WSA)
It is an IBM research prototype of an 802.11 wireless LAN security auditor, Running on Linux on an Iraq PDA (Personal Digital Assistant). WSA helps Network administrators to close any vulnerability by automatically audits A wireless network for proper security configuration. While there are other 802.11 network analyzers such as Ethereal, Snuffer and Wampum, WSA Aims at protocol experts who want to capture wireless packets for detailed Analysis. Moreover, it is intended for the more general audience of Network installers and administrators, who want a way to easily and Quickly verify the security configuration of their networks, without having to Understand any of the details of the 802.11 protocols
Wireless Channels
IEEE 802.11g/b wireless nodes communicate with each other using radio frequency signals in the ISM (Industrial, Scientific, and Medical) band between 2.4 GHz and 2.5 GHz. Neighboring channels are 5 MHz apart. However, due to the spread spectrum effect of the signals, a node sending signals using a particular hannel will utilize frequency spectrum 12.5 MHz above and below the center channel frequency. As a result, two separate wireless networks using neighboring channels (for example, channel 1 and channel 2) in the same general vicinity will interfere with each other. Applying two channels that allow the maximum channel separation will decrease the amount of channel cross-talk and provide a noticeable performance increase over networks with minimal channel separation. The preferred channel separation between the channels in neighboring wireless networks is 25 MHz (five channels). This means that you can apply up to three different channels within your wireless network. In the United States, only 11 usable wireless channels are available, so we recommended that you start using channel 1, grow to use channel 6, and add channel 11 when necessary, because these three channels do not overlap.
Wide Area Network Security
Wireless LAN’s will make use of the most secure encryption and authentication facilities available
Users will not install their own wireless equipment under any circumstances.
Dial-in modems will not be used if at all possible. If a modem must be used dial-back modems should be used. A secure VPN tunnel is the preferred option.
Modems will not be used by users without first notifying the I.T. Department and obtaining their approval.
Where dial-in modems are used, the modem will be unplugged from the telephone network and the access software disabled when not in use.
Modems will only be used where necessary, in normal circumstances all communications should pass through the Organization’s router and firewall.
Where leased lines are used, the associated channel service units will be locked up to prevent access to their monitoring ports.
All bridges, routers and gateways will be kept locked up in secure areas.
Unnecessary protocols will be removed from routers.
The preferred method of connection to outside Organizations is by a secure VPN connection, using IPSEC or SSL.
All connections made to the Organization’s network by outside organizations will be logged.
WEP Wireless Security
The absence of a physical connection between nodes makes the wireless links vulnerable to eavesdropping and information theft. To provide a certain level of security, the IEEE 802.11 standard has defined two types of authentication methods, Open System and Shared Key. With Open System authentication, a wireless computer can join any network and receive any messages that are not encrypted. With Shared Key authentication, only those computers that possess the correct authentication key can join the network. By default, IEEE 802.11 wireless devices operate in an Open System network. Recently, Wi-Fi, the Wireless Ethernet Compatibility Alliance) developed the Wi-Fi Protected Access (WPA), a new strongly enhanced Wi- Fi security. WPA will soon be incorporated into the IEEE 802.11 standard. WEP (Wired Equivalent Privacy) is discussed below, and WPA is discussed on.
Wide Area Network Security
The 802.11 standard defines several services that govern how two 802.11 devices communicate. The following events must occur before an 802.11 station can communicate with an Ethernet network through an access point such as the one built in to the NETGEAR product: 1. Turn on the wireless station. 2. The station listens for messages from any access points that are in range. 3. The station finds a message from an access point that has a matching SSID. 4. The station sends an authentication request to the access point. 5. The access point authenticates the station. 6. The station sends an association request to the access point. 7. The access point associates with the station. 8. The station can now communicate with the Ethernet network through the access point. An access point must authenticate a station before the station can associate with the access point or communicate with the network. The IEEE 802.11 standard defines two types of WEP authentication: Open System and Shared Key. • Open System Authentication allows any device to join the network, assuming that the device SSID matches the access point SSID. Alternatively, the device can use the “ANY” SSID option to associate with any available access point within range, regardless of its SSID. • Shared Key Authentication requires that the station and the access point have the same WEP key to authenticate. These two authentication procedures are described bell.
How Does WPA Compare to WEP?
WEP is a data encryption method and is not intended as a user authentication mechanism. WPA user authentication is implemented using 802.1x and the Extensible Authentication Protocol (EAP). Support for 802.1x authentication is required in WPA. In the 802.11 standard, 802.1 x authentications was optional. For details on EAP specifically, refer to IETF RFC 2284. With 802.11 WEP, all access points and client wireless adapters on a particular wireless LAN must use the same encryption key. A major problem with the 802.11 standard is that the keys are cumbersome to change. If you do not update the WEP keys often, an unauthorized person with a sniffing tool can monitor your network for less than a day and decode the encrypted messages. Products based on the 802.11 standard alone offer system administrators no effective method to update the keys. For 802.11, WEP encryption is optional. For WPA, encryption using Temporal Key Integrity Protocol (TKIP) is required. TKIP replaces WEP with a new encryption algorithm that is stronger than the WEP algorithm, but that uses the calculation facilities present on existing wireless devices to perform encryption operations. TKIP provides important data encryption enhancements including a per-packet key mixing function, a message integrity check (MIC) named Michael, an extended initialization vector (IV) with sequencing rules, and a re-keying mechanism. Through these enhancements, TKIP addresses all known WEP vulnerabilities.
However, this extension of physical boundaries provides expanded access to both authorized and unauthorized users that make it inherently less secure than wired networks.
WLAN vulnerabilities are mainly caused by WEP as its security protocol. However, these problems can be solved with the new standards, such as 802.11i, which is planned to be released later this year. For the time being, WLAN users can protect their networks by practicing the suggested actions that are mentioned in this paper based on the cost and the level of security that they wish However, there will be no complete fix for the existing vulnerabilities. All in all, the very best way to secure WLAN is to have the security knowledge, proper implementation, and continued maintenance.
How Does WPA Compare to IEEE 802.11i?
WPA is forward-compatible with the IEEE 802.11i security specification currently under development. WPA is a subset of the current 802.11i draft and uses certain pieces of the 802.11i draft that were ready to bring to market in 2003, such as 802.1x and TKIP. The main pieces of the 802.11i draft that are not included in WPA are secure IBSS (Ad-Hoc mode), secure fast handoff (for specialized 802.11 Void phones), as well as enhanced encryption protocols such as AES-CCMP. These features are either not yet ready for market or will require hardware upgrades to implement
What are the Key Features of WPA Security?
The following security features are included in the WPA standard: • WPA Authentication • WPA Encryption Key Management – Temporal Key Integrity Protocol (TKIP) – Michael message integrity code (MIC) – AES Support • Support for a Mixture of WPA and WEP Wireless Clients These features are discussed below. WPA addresses most of the known WEP vulnerabilities and is primarily intended for wireless infrastructure networks as found in the enterprise. This infrastructure includes stations, access points, and authentication servers (typically Remote Authentication Dial-In User Service servers, called RADIUS servers). The RADIUS server holds (or has access to) user credentials (for example, user names and passwords) and authenticates wireless users before they gain access to the network. The strength of WPA comes from an integrated sequence of operations that encompass 802.1X/ EAP authentication and sophisticated key management and encryption techniques. Its major operations include:
• Network security capability determination.
This occurs at the 802.11 level and is communicated through WPA information elements in Beacon, Probe Response, and (Re) Association Requests. Information in these elements includes the authentication method (802.1X or Pre-shared key) and the preferred cipher suite (WEP, TKIP, or AES, which is Advanced Encryption Standard). The primary information conveyed in the Beacon frames is the authentication method and the cipher suite. Possible authentication methods include 802.1X and Pre-shared key. Pre-shared key is an authentication method that uses a statically configured passphrase on both the stations and the access point. This removes the need for an authentication server, which in many home and small office environments is neither available nor desirable. Possible cipher suites include: WEP, TKIP, and AES. We say more about TKIP and AES when addressing data privacy below.
• Authentication. EAP over 802.1X is used for authentication.
Mutual authentication is gained by choosing an EAP type supporting this feature and is required by WPA. The 802.1X port access control prevents full access to the network until authentication completes. The 802.1X EAPOL-Key packets are used by WPA to distribute per-session keys to those stations successfully authenticated
Discussions
I was selected to work with IT department in Sonagon plaza, (3rd Floor)West Panthapath,Dhanmondi,Dhaka-1215.I reported to the concern manager and was sent to K.Kalam who is the Admin Director in China-Bangla Group.
This internship introduces me with the rules & regulation of an office. Being attached with LAN issues & security .Most of the critical problems are done by the LAN issues & security team & third party or local vendor’s joint venture. So the main duty of system operation is to solve the problem & supervise the vendor’s works. LAN issues & security team should be very careful about their works because if a vendor makes any mistake the responsibility goes on them. I also did some works with the Payment schedule & did of agreement team whose works is to maintain the general problems.
Before my internship I didn’t have any practical knowledge about Real Estate Company & their works. The outcome of this internship rang from learning the very basic concepts of LAN issue &security solution to analyzing the very partial and operational state of affairs like; got to the opportunity to observe LAN fault & management procures & also gathered knowledge about setup & maintenance.
The work environment of the office was very friendly. I didn’t feel like an outsider working there because all of them treated me as one of them. Through this period of my internship I asked a lot of questions queries to many of them and they answered those generously. Specially my supervisor helped me a lot and gave me idea about my future life of job. At last I want to say that I’m very fortunate to get such a great opportunity to work with such a good organization.
Conclusions
The general idea of WLAN was basically to provide a wireless network Infrastructure comparable to the wired Ethernet networks in use. It has since Evolved and is still currently evolving very rapidly towards offering fast connection Capabilities within larger areas. However, this extension of physical boundaries provides expanded access to both authorized and unauthorized users that make it inherently less secure than wired networks.
WLAN vulnerabilities are mainly caused by WEP as its security protocol. However, these problems can be solved with the new standards, such as 802.11i, which is planned to be released later this year. For the time being, WLAN users can protect their networks by practicing the suggested actions that are mentioned in this paper based on the cost and the level of security that they wish.