Basic objective of this lecture is to describe on Hubs and Switches according to Router. Hubs indicates only one transmission at a time. Transmission from a station received by central hub and re transmitted on all outgoing lines. Layer 2 Switches are: Flat address space, Broadcast storm and only one path between any 2 devices. Routers connect to several networks, including backbone networks of inter-connected routers. These networks may be of different (data link) types like; Ethernet, Token Ring, FDDI etc.
EEE
General objective of this lecture is to explain Layered Architectures. Here briefly describe schemes for Organizing the Responsibility of Networking Components and provide a layered abstraction for networking. This also focus on Network Service Model and OSI Reference Model. A layered service model developed by the International Standardization Organization (ISO). Finally explain seven layers, they are (highest to lowest level): Application, Presentation, Session, Transport, Network, Data link and Physical.
General purpose of this lecture is to describe Internet Implementation tips. The network protocols upon which application-level protocols are built, like, HTTP, SMTP, IMAP (Internet Message Access Protocol. TCP/IP is the framework for the Internet. TCP/IP is actually two protocols: TCP: Transport control protocol and IP: Internet protocol. Here also also explain on Internet Messaging.
Major objective of this lecture is to describe Internet History. Internet was Developed by Advanced Research Projects Agency (ARPA). Became a useable internet in 1977. The University of California (at Berkeley) incorporated TCP/IP programming into its BSD UNIX operating system in 1983. Public Internet became practical for private organizations to connect to the Internet (mid-late 1980s), due to inexpensive hardware.
Principle purpose of this lecture is to explain Network Properties. here briefly describe some important Network Properties, like; Scope, Scalability, Robustness, Self-Stabilization, Autoconfigurability, Safety, Configurability, Determinism, Migration etc. This lecture also explain on Network Usage. If network resources are unused, the network is not being used efficiently. Unused network resources could be used to provide higher throughput to hosts.
Networking is a connection between two or more computers, even when you connect two computers via a USB cable. Networks use standardized hardware, like Twisted pair cabling and Ethernet hubs, ATM switches and optical fibre cabling. Internetworking is a connection between two or more networks, like an Ethernet network connected to another Ethernet network by glass fibre cable and ATM switches. This lecture also briefly describe on Network Speed and Local Area Network (LAN).
Basic purpose if this lecture is to describe on Router Architecture. Here briefly explain Hardware components of a router and Commercial routers. Hardware components of a router include: Network interfaces, Interconnection network and Processor with a memory and CPU. Commercial routers include: Interconnection network and interface cards are sophisticated, Processor is only responsible for control functions (route processor) and Almost all forwarding is done on interface cards.
Router Network Switch
Before the year 2000, the majority of the public had no idea what any of these devices were. Since the introduction of broadband Internet connections, these devices have gained popularity. Just about everyone knows what a router is now. Or as some people like to pronounce them “rooters.” While they all perform different tasks, each device plays an important role in networking. In the duration of this article, I will discuss each device individually. Then, I will discuss any similarities and differences between each device.
Hubs
The network hub has been around for ages. These devices are sometimes referred to as repeaters. A hub sees information in the form of bits. Using a hub is now the cheapest way to connect devices. Hubs work by broadcasting network traffic across all ports. For example, an 8 port hub will broadcast data across all 8 ports even though the data is meant to travel between two devices. For this reason, hubs incur an increased amount of collisions. A collision is simply the results of two devices (computers) trying to broadcast simultaneously. Collisions are a normal part of network traffic. Ethernet itself is a collision based technology. The image below shows a simple network hub.
Switches
Switches have become more complex with increased popularity of high-speed networks. They can range in price for around $30 to well in the $1000s. However, in recent years the prices of switches has dramatically decreased. Switches perform the same functionality of hubs, except they only send data to intended ports. Unlike a hub, a switch will not broadcast data across the entire switch. As a result, switches will not suffer from a high rate of collisions. High-end switches offer advanced functionality such as VLAN management. Complex networks will use several layers of switches of pass along large amounts of network traffic. The image below shows a simple network switch. Notice that it is similar in appearance to the hub above. Physically, the switch is a little taller and deeper. These switches usually contain 1 or more cooling fans and can be quite loud.
Routers
Routers are the smartest of the 3 devices. They make intelligent decisions on how to route traffic. Routing protocols are composed of different algorithms that direct the way routers move traffic. These devices can range from around $30 to well in the $1,000,000s. The Internet itself uses complex routers fed by fiber optics to connect cities and countries together. Routers play the most important role in operating a network. They are the most dynamic of all 3 devices mentioned in this article. They can work with or act as firewalls. The image below shows a low-end Cisco router:
Switch vs. Hub
Think of it like this, a hub is like getting spam. You have an address, but the spammers don’t know you personally, they just know you exist and send you mail regardless. On the other hand, legit mail is sent by someone that intends to send you an important piece of information. Think of the post office as a switch. All the mail is sent through them. They sort it based on name and address, then it’s delivered. Make Sense?
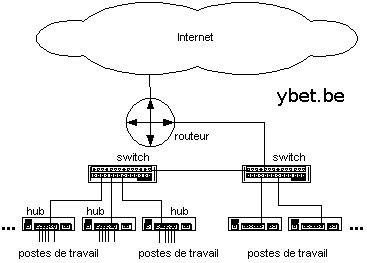
Up to now, we used the term “network concentrators” to indicate the networks “noeuds” in T Bases 10, T bases 100, gigabits… (excepting coaxial networks which uses bus topology). This view is too simple. The Ethernet concentrators gathers the hub, the switch, routers… On the level installation, the technique of wiring is almost the same one. Concentrator choice varies according to the importance of the network, the site of the concentrator and the importance (interconnection) of networks.
2. Hub
Hub are used in Ethernet bases 10 and bases 100. Hub is the simplest concentrator. It is practically only one repeater (it is its French name). It amplifies the signal to be able to transfer it towards all connected PC. All information arriving on the equipment is thus transmited on all the lines. In the case of important networks by the number of connected PC or the importance of the flow of transferred information, one cannot use HUB. Indeed, as soon as a PC says something, everyone hears it and when each one starts to transmit, speeds decrease directly. The HUB are characterized by a number of connection: 4, 5, 8, 10, 16, 24…
According to the version and the model, they integrate some characteristics of connection specific to the apparatus.
Hubs bases 10: connection numbers according to the model, port reverse (this one makes it possible to connect two Hubs between-them, avoiding the use of a cross cable RJ45), a connection coaxial. By connection, one finds a led announcing connection to a chart and a led of collision per channel or for the unit. The latter announces the state of the whole of connections.
Hubs bases 100: connection numbers according to the model, port reverse (this one makes it possible to connect two Hubs between-them), never of connection coaxial. By connection, one finds a LED announcing connection to a chart and a led of collision per channel or for the unit. The latter announces the state of the whole of connections. Moreover, for versions 10/100, one finds two LED for each channel (bases 10 and bases 100)
A last remark, according to the standard, the maximum number of HUB in cascade (connected port to port, by stackable types) is limited to 4 between 2 stations for the 10 base T and to 2 for the 100 base T. This is related on the maximum travel time of an ETHERNET signal before its disappearance and to the time of detection of the collisions on the cable. It could be that the collision is not detected in time and that the second transmitting station sends the message by thinking that the way is free. This does not exist for the switch “blind and forward” which record the screens before sending them and segment the network according to connections, avoiding these collisions.
3. Network switch.
Introduction
Of appearance, it is equivalent to a HUB.
The HUB’S default is that all information forwards towards all the PC. A switch recognizes the various computers, servers, routers, printers and firewall connected on the network. By receiving information, it decodes the heading to know the recipient and sends it only towards this one in the case of a connection PC towards PC. This reduces the traffic on the complete network. With the difference, information all circulates on all wiring with the hub’ S and thus towards all the connected stations. They thus work on level 1, 2 and 3 of OSI model, for only layers 1 in the case of the HUBS. Level 3 of OSI model determines the roads of transport. The switch replace the HUBS more and more. The prices become practically equivalent.
The majority of the switch can use the duplex Full mode. The communication is then bi-directional, doubling the rate of maximum transfer. This function is never established in the HUB. Switch checks automatically if the connected peripheral is compatible full or half duplex. This function is often taken again under the denomination “Car Negotiation“.
The current models of switch are often Auto MDI/MDIX. This means that the port will automatically detect the crossing of the cables for connection. In the case of the HUB, a port provided with a pushbutton, includes the function manually. You can nevertheless use cables crossed to connect concentrators between them.
The use of the switch makes it possible to reduce the data collisions on wiring network. When a peripheral attempt to transmit data, it sends a message on wiring. If another peripheral communicates already, two messages are found at the same time on the network. The first takes again its message at the beginning and the second awaits for trying again a few milliseconds later.
There are (in theory) no limitations of the number of switch in cascade on a network.
Operation of a switch.
To starting, a switch will build a table of correspondence addresses MAC – port connection number. This table is an internal memory storage of the switch. For example for D-link DSS-16+ (16 ports), it is of 8000 entries (stations). By against, for a model of lower range (D-Link OF the -1024D of 24 ports) it is also of 8000 entries, for the majority of the switches 5 ports, it varies from 512 to 1000 entries. This does not pose problems for a small network but well for large networks. In any event, the maximum number of connected PC is limited by the class of address IP used. When a new chart will be connected on one of its ports, it will adapt its table. The performances of the switch are thus tributary of the importance of this table.
Let us see now what occurs when a PC (PC1) communicates towards another PC (PC2) connected on same the switch. The starting message including the TO address, the switch will find directly in its table the address of the PC2 and will redirect the message on the adequate port. Only the wiring of 2 ports (PC1 and PC2) will be to use. Other PC will be able to communicate at the same time on the other ports.
 Now let us see the case or the network uses 2 switch. The PC1 sends the message with the TO address on the switch1 on which it is connected. The switch will check in its table if the TO address is physically connected on one of its ports in its table. In our case it is not the case. The switch thus will send a special message (an address MAC FF.FF.FF.FF.FF.FF, called broadcast) on all its ports to determine on which port the peripheral of destination is. This broadcast generally passes on all the network. While receiving the broadcast, the switch 2 will check in its table if the TO address is in its table. In our case, it is present. It thus will return a message to the switch 1 meaning that the message is for him. The switch 1 thus will direct the message towards the port connected to the switch 2. The switch 1 will memorize in its table the address of the PC2 and the associated port (in our case that of the switch 2). This does not pose too many problems as long as the capacity of the table of the switch 1 is sufficient.
Now let us see the case or the network uses 2 switch. The PC1 sends the message with the TO address on the switch1 on which it is connected. The switch will check in its table if the TO address is physically connected on one of its ports in its table. In our case it is not the case. The switch thus will send a special message (an address MAC FF.FF.FF.FF.FF.FF, called broadcast) on all its ports to determine on which port the peripheral of destination is. This broadcast generally passes on all the network. While receiving the broadcast, the switch 2 will check in its table if the TO address is in its table. In our case, it is present. It thus will return a message to the switch 1 meaning that the message is for him. The switch 1 thus will direct the message towards the port connected to the switch 2. The switch 1 will memorize in its table the address of the PC2 and the associated port (in our case that of the switch 2). This does not pose too many problems as long as the capacity of the table of the switch 1 is sufficient.
Let us see some more complex cases now. When a MAC address off-line on line is placed in the table, the switch will keep it during a certain time. If a new request towards this address is received, the wearing of destination is found in the table. On the other hand, if the time between the requests is too long (generally 300 seconds), the entry of the table is erased and the process of broadcast is again activated. Inevitably, if the table is too small (case of Switch with a low number of ports on a very important network), the MAC entry in the perhaps prematurely unobtrusive table.
These characteristics of tables reduced in the switch of bottom-of-the-range installation of big problems in the networks. Moreover, less the switch comprises of entry, plus the table is small. This implies that for the use of small switches (4-8 ports), the number of switch connected between-them for a connection between 2 PC is limited. I have already had the problem in a network of 30 PC. As soon as the factory started, the communications networks broke down. The replacement of switch by HUB for the most distant stations solved the problem but one could have used switch of better quality.
All the switch are not equivalent. For networks of ten stations, the problem does not arise. On the other hand, for the important networks, the switch of medium and high range correct better the attenuations of the signals received before transmission.
Types of switch
The technology of a switch is closely related on the type of data, the topology of the network and the desired performances.
The first process of operation and more running, called Blind and Forward, store all the screens before sending them on the adequate port. Before storing information, the switch carries out various operations, energy of the detection of error (RUNT) or construction of the table of addresses until the functions applicable to level 3 of OSI model, such as filtering within a protocol. This mode is appropriate well for the client/server mode because it does not propagate an error and accepts the mixture of various media of connection. This explains why one uses them in the mixed environments coppers/fiber or in the mixture of flows. The storage capacity plug varies from 256 KB to more than 8 MB for the largest models. Small the switch of this type often shares the storage capacity by groups of ports (for example by 8 ports). On the other hand, the models of high range use a memory dedicated by wearing of entry. The latency between the reception and the sending of a message depends on the size of the data. This slows down the transfer of the large files.
The mode Cut Through analyzes only the Mac address of destination (placed in heading of each screen, coded on 48 bits and specific to each chart network) then redirects the flood of data without any checking. This type of switch does not make any checking on the message itself. In the principle, the destination address must be stored beforehand in the table, if not a mechanism of broadcast is found. These switch is only used in environments made up of point-to-point connections (customers – server). One exclude all mixed applications from type peer to peer.
The mode Cut Through Runt Free is derived from Cut Through. When a collision occurs on the network, an incomplete screen (less than 64 bytes) called Runt is delivered by the switch. In this mode, the switch analyzes the first 64 bits of screens before sending them to the recipient. If the screen is rather long, it is sent. In the contrary case, it is ignored.
The mode Early Cut Through (also called Free Fragment at Cisco) is also derived from Cut Through. This system directly transmits the screens whose TO address is detected and present in the table of address of the switch. For that, the table must be perfectly up to date, which is difficult in the case of large networks. On the other hand, it will not send the screens whose TO address is not clearly identified. It does not hold account either of the original address. The latencies are very low.
The mode Adaptive Cut Through is distinguished especially on the level from the correction from the errors. These switches keep the trace of the screens comprising of the errors. When the error count exceeds a certain threshold, the switch passes automatically in mode Store and Forward. This mechanism avoids the propagation of the errors on the network by isolating certain segments from the network. When the error rate becomes again normal, the switch returns to the mode Cut Through.
Additional characteristics
Switch can be stackable (stackable). In this case, a special connector makes it possible to connect several switch of the same mark between-them. The number of switch piled up (of the same model) is limited. The whole of the group of switch is seen like only one switch. This makes it possible to increase the number of ports and to take again a more important common table. The HUB are not truly stackables since this would return exactly to same as to inter-connect them with cross cables).
Some switch are manageables (more information). By an interface of the WEB type connected to address IP of the switch or by RS232 and the use of telnet, you can block certain lines, preventing for example, a part of PC to connect itself towards another block of PC or to determine physically which computer has access to which server. This also makes it possible to determine beaches of addresses on ports (case where several switch – Hub are chained) and thus to increase speed. A small remark nevertheless, management is generally done according to the MAC addresses (single and given with the manufacture of the chart network or the peripheral). The use of these characteristics must be considered with precaution since if you change a chart network, the switch will have to be reconfigured. Certain models make it possible nevertheless to create user groups by using protocol IGMP. They are known as of level 2 (to level 2 of OSI model) if they make it possible to determine the addresses and of level 3 (to level 3 of OSI model) if they allow in more of blocking by ports (TCP or UDP).
Via interface IP or telnet, a switch manageable also makes it possible to remotely check connections on the switch (posting of the front face), to safeguard or restore the configuration, update of the firmware, to parameterize the lifespan of the MAC addresses in the table…
Some switch of the type Cut Through integrate additional functions as Meshing which makes it possible to create a table on several switch (and not to more send information on all the ports when the apparatus of destination is not directly connected) on the switch. The Trunking Port makes it possible to reserve a certain number of ports for connections between 2 switches.
Routers
The hub and switch make it possible to connect equipment forming part of the same class of address in IP or of the same sub-network (other protocols). For recall, an address IP of an apparatus connected to a network is single. It is of type X.X.X.X, for example 212.52.36.98. Values X can vary from 0 to 255. Address IP consists of 32 bits and a mask also coded on 32 bits.
One determined hierarchies in the addresses, called classes of address.
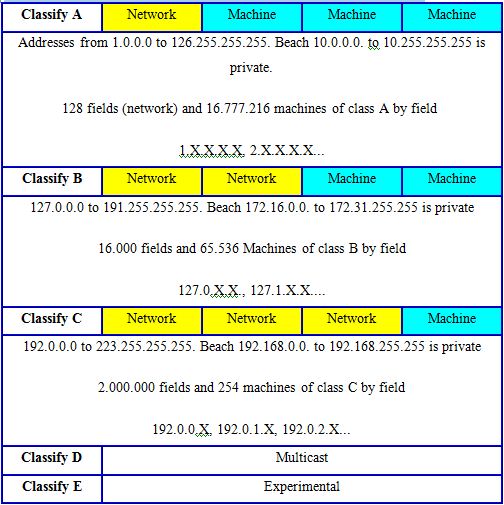
The addresses finishing by 0 or 255 are not usable directly.
On the other hand, the connection of a PC with address 192.168.1.23 (class C) will have to pass through a router to communicate with an installation located into 15.63.23.96 (class A). This is the case for a PC which is connected to an Internet site (using addresses of classes A or B). In the same way, in an internal network, the connection of two stations in networks of different classes C (for example 192.168.223 and 192.168.3.32) must pass through a router. A network without router is thus limited to 254 stations (0 and 255 are not used).
In the same way; as the addresses of Internet sites can practically be in all the beaches of addresses A and class B, the connection of an internal network with Internet passes obligatorily through a router which serve of gateway
Nothing obliges to use the addresses of classes C for an internal network, but it is preferable.
Notice, the class of address 169.254.XXX.XXX is not usable in an internal network for a division Internet, this beach of particular address does not accept it even if it is often given by defect by DHCP of Windows.
The router is practically a computer with him all alone. This one decodes the screens and recognizes parts information of the headings and can thus transmit information on other routers who renew information towards the recipients.
A router joins together networks on the level of the layer network (layer 3), it allows to connect 2 networks with a “barrier” between the two. Indeed, it filters information to send only what is indeed to intend for the following network. The most current use is the connection of multiple stations towards Internet. The data forwarding on the local area network (not intended for Internet) are not transmitted outside. Moreover, the routers partly allow to hide the network. Indeed, in a connection Internet for example, the supplier of access gives an address TCP/IP which is assigned to the router. This one, by the means of a technology NAT / STALEMATE (Network address translation/port address translation) goes redirect the data towards the private address which is assigned to the PC.
The routers are skeletal and in particular allow to block certain connections. Nevertheless, it do not ensure of safety the level of ports TCP or UDP. They are used to interface various groups of PC (for example departments) by ensuring a pretence of safety. Some switch of manageable can partly be to use for this function as long as the network remains in the same class of addresses. The principal use in SME is the division of a connection Internet, but of others exist like network under following Win98 and or specific equipment.
The routers are not useful that to connect networks to Internet, they also make it possible to be used as bridge (English Bridge) to connect itself to a corporate network. The future connections for this protected kind of application go rather for the VPN via Internet. We will see this in chapter 10: Distant connections
It is not possible to connect 2 networks directly by connecting 2 charts networks in a central PC, except by using a software of connection proxy of the Wingate type.
A DHCP server (Dynamic Host Protocol Configuration) can be established in manner software (Windows 2000 for example) or in a router. This possibility makes it possible automatically to allot IP addresses to each station in a beach of given address (in the same class of address).
5. Repeaters
The repeater is equipment which makes it possible to exceed the maximum length imposed by the standard of a network. To be done it amplifies and regenerates the electric signal. It is also able to insulate a failing section (open Cable for example) and to adapt two different Ethernet media. (For example 10base2 towards 10BaseT). This last use which is currently the principal one.
For the connections monomode 1000Base LX, there is allowing apparatus of the connections of more than 100 kilometers.
6. Passage of IP addresses to the MAC addresses
We know already that the communications are done by the MAC addresses and not directly by IP addresses.
For a communication, the transmitting PC checks if the PC is in the same class of address IP. If it is the case, it will send a ARP command to determine the MAC address of destination and directly sends the packet data and the headings on the network. The HUBS leave the packet just as it is since they are simple amplifiers. On the other hand, if the network is connected by switches, each switch will check the MAC address in its table, if required to send a broadcast.
On the other hand, if the PC of destination is not in the same class of address, it sends the packet to the router (of which the address MAC is known) with address IP of destination. The router will check if he is connected to the sub-network (class IP) of destination. If it is directly connected, it sends information to the recipient via a ARP. In the contrary case, it will send the packet to the following router, and so on.
7. Connection of an Ethernet network.
By the part Ethernet connection, we know already that:
1. To connect 2 hubs (switch) between-them, we must use a cross cable. Nevertheless, a small push rod switch is often present on one of the ports which makes it possible to use a normal cable. The new models detect the crossing also automatically.
2. In Ethernet 10, 4 Hubs present a blocking at the level speeds of connection.
3. In Ethernet 100, 2 HUBS in series start to cause “stoppers” in the data flows.
4. The maximum distances must be respected (100 meters maximum for the cable).
5. The rules of wiring must be strict: connectors, proximities of the electric cables, networks.
Let us pass now to a real Ethernet network.
With. The departments (or offices, or stages) can be connected by a HUBS or a switch. If all connections are made PC towards only one server, Hubs can be sufficient. On the other hand, in the event of use of other peripherals (printers network for example), a switch is definitely preferable. The HUB or the SWITCH must have a sufficient number of ports. In the case of a small single application customers – 1 server, as all the communications go towards only one PC (the server), the use of switch or Hub is practically equivalent, except if that the use of a switch will reduce the number of collisions. The switch can also be duplex Full (bi-directional communication)
B. The departments between-them can be connected by HUBS or switch, but the preference must go to switch, if possible manageable which make it possible to block certain connections. All external connections (Internet and inter-network connection) requires a router. The case of divisions Internet directly on a PC connected to Internet must be proscribed for the companies (division by Windows), mainly in the event of heavy networks of type Win NT or Netware. Indeed, the routers include the function NAT which makes it possible to mask the various addresses of the network interns and include more and more bases of safety intrusions of the type firewall hardware.
Principle purpose of this lecture is to explain basics of Wireless Sensor Network. There are Four Basic Components in a sensor network: An assembly of distributed or localized sensors; An interconnecting network (usually, but not always, wireless-based); a central point of information clustering; and a set of computing resources at the central point (or beyond) to handle. Here also briefly describe background of Sensor Network Technology and applications of Sensor Networks.
General objective of this lecture is to describe on Security in Wireless Sensor Network (WSN). WSN consists of spatially distributed autonomous sensor nodes to monitor physical or environmental conditions, such as temperature, sound, pressure, motion or pollutants and to cooperatively pass their data through the network to a main location. Here also briefly explain Threats to WSN, WSN operational paradigms, Key distribution techniques for WSN and Various key distribution schemes.