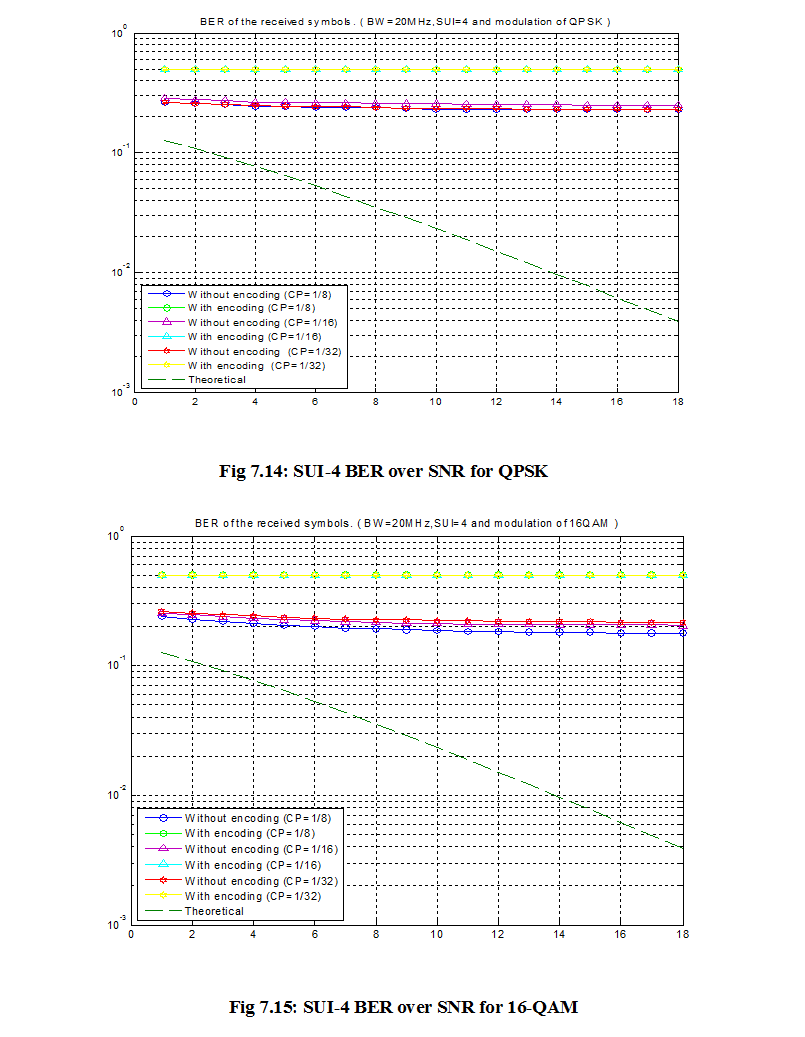
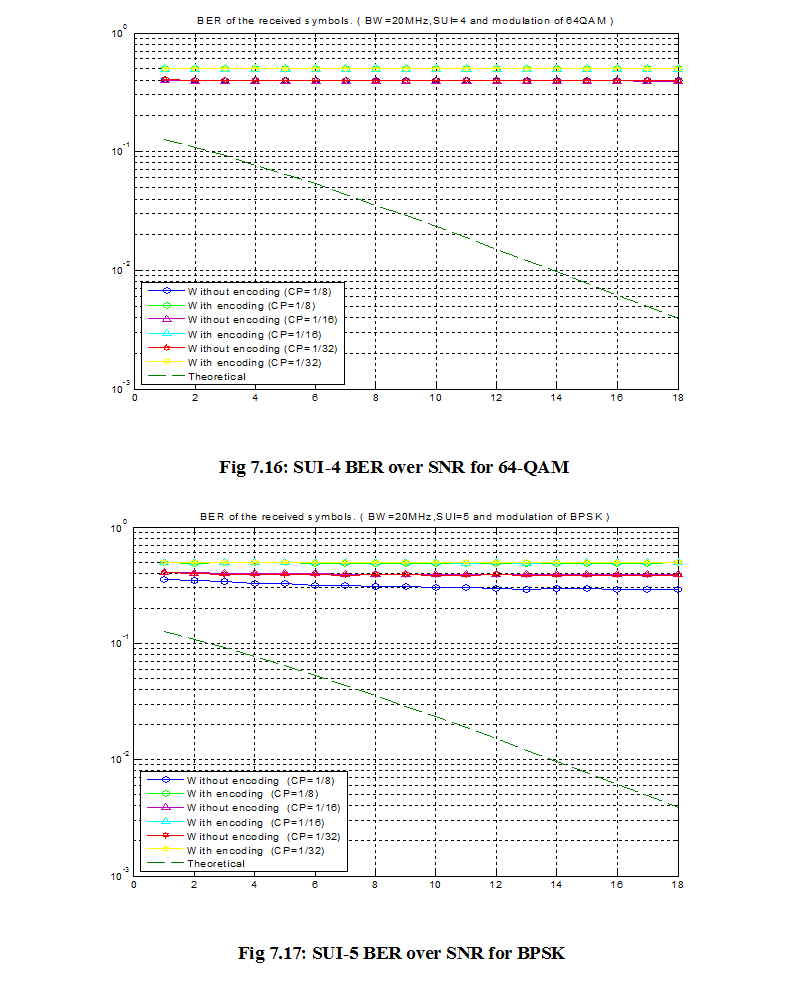
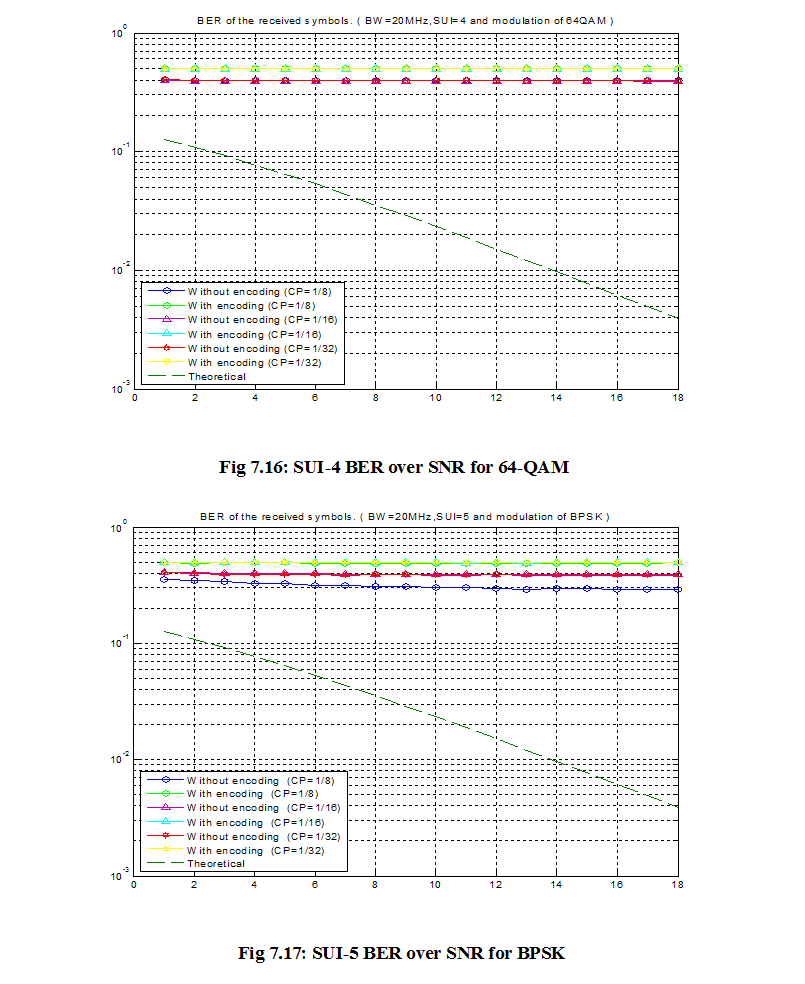
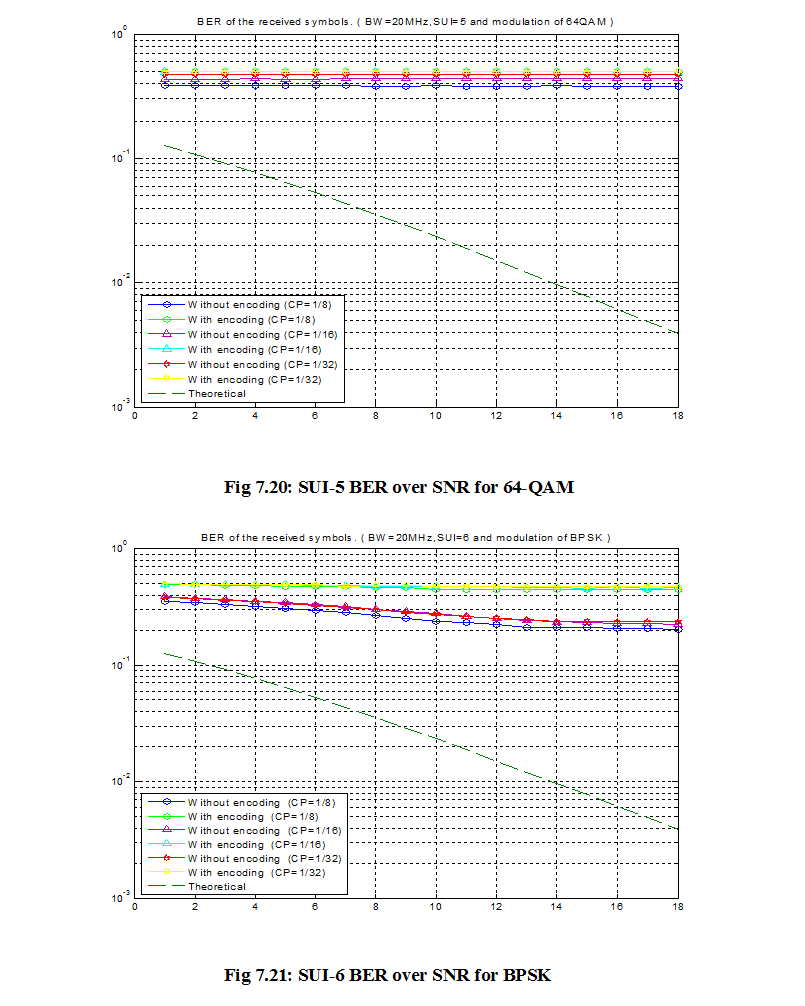
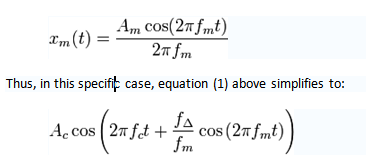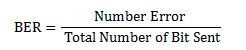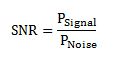Introduction:
In a broad sense, the term communications refers to the sending, receiving and processing of information by electronic means. Communication started with wire telegraphy in the eighteen forties, developing with telephony some decades later and radio at the beginning of the century. Radio communication, made possible by the invention of the triode tube, was greatly improved by the work done during world war 2.It subsequently became even more widely used and refined through the invention use of the transistor, integrated circuits and other semiconductor devices. More recently the, use of satellite and fiber optics has made communications even more widespread, with an increasing emphasis on computer and other data communications.
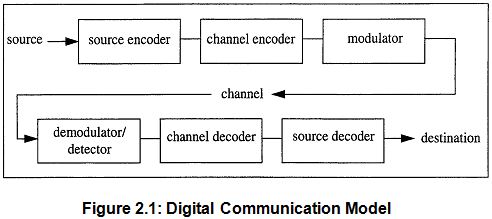
A modern communications system is first concerned with the sorting, processing and sometimes storing of information before its transmission. The actuals transmission then follows, with further processing and the filtering of noise. Finally we have reception, which may include processing step such as decoding, storage and interpretation.
In order to become familiar with these systems, it is necessary first to know about amplifiers and oscillators, the building blocks of all electronics processes and equipment. With these as a background, the everyday communications concepts of noise, modulation and information theory, as well as the various systems themselves, may be approached. Any logical order may be used, but the one adopted here is, basic system, communication processes and circuits, and complex systems, is considered most suitable. It is also important to consider the human factors influencing a particular system, since thy must always affect in design, planning and use.
The project – “Design and implementation of a Frequency Shift Keying transmitter and receiver” is designed for undergraduate student. In this project student’s will get a solid overview of communication system, types, technique, transmitter, receiver, FSK modulation, demodulation, and modulator and demodulator circuit.
About this Project
In this project transmission of message signal is a simplexformofwireless communication. Here a FSK transmitter is interfaced with a microcontroller to generate the message signal. In the receiver section another microcontroller is used to display the message signal.
Objectives
1. To gather theoretical and practical knowledge about communication system and circuit
2. Identify available methods and technique for FSK modulation, demodulation and
corresponding circuits.
3. Establish a suitable process for implementing this project.
4. Produce a system to occur transmission and reception of digital signal.
5. Use design patterns, standards and best practices where appropriate.
6. And finally test this entire system.
Why this Project?
Communication engineering means transmission of message signal from one place to another place. As a student of electronics and communication engineering our main goal is to design a system that is very much related to the main theme of the communication engineering.
This system is a simplex form of communication. It works like one way broadcasting system.so we can called it a one kind of pager. Our country is progressing technologically day by day. Our system can be applied as an alternative of pager into a small building.
For above reasons we choose this project.
Literature review
History of Communication
Early telecommunications
In the middle Ages, chains of beacons were commonly used on hilltops as a means of relaying a signal. Beacon chains suffered the drawback that they could only pass a single bit of information, so the meaning of the message such as “the enemy has been sighted” had to be agreed upon in advance. One notable instance of their use was during the Spanish Armada, when a beacon chain relayed a signal from Plymouth to London signaling the arrival of Spanish ship.
In 1792, Claude Chappe, a French engineer, built the first fixed visual telegraphy system (or semaphore line) between Lille and Paris. However semaphore suffered from the need for skilled operators and expensive towers at intervals of ten to thirty kilometers (six to nineteen miles). As a result of competition from the electrical telegraph, the last commercial line was abandoned in 1880.
Telegraph and telephone
The first commercial electrical telegraph was constructed by Sir Charles Wheatstone and Sir William Fothergill Cooke and opened on 9 April 1839. Both Wheatstone and Cooke viewed their device as “an improvement to the [existing] electromagnetic telegraph” not as a new device.
Samuel Morse independently developed a version of the electrical telegraph that he unsuccessfully demonstrated on 2 September 1837. His code was an important advance over Wheatstone’s signaling method. The first transatlantic telegraph cable was successfully completed on 27 July 1866, allowing transatlantic telecommunication for the first time.
The conventional telephone was invented independently by Alexander Bell and Elisha Gray in 1876. Antonio Meucci invented the first device that allowed the electrical transmission of voice over a line in 1849. However Meucci’s device was of little practical value because it relied upon the electrophonic effect and thus required users to place the receiver in their mouth to “hear” what was being said. The first commercial telephone services were set up in 1878 and 1879 on both sides of the Atlantic in the cities of New Haven and London.
Radio and television
In 1832, James Lindsay gave a classroom demonstration of wireless telegraphy to his students. By 1854, he was able to demonstrate a transmission across the Firth of Tay from Dundee, Scotland to Woodhaven, a distance of two miles (3 km), using water as the transmission medium. In December 1901, Guglielmo Marconi established wireless communication between St. John’s, Newfoundland (Canada) and Poldhu, Cornwall (England), earning him the 1909 Nobel Prize in physics (which he shared with Karl Braun).[11] However small-scale radio communication had already been demonstrated in 1893 by Nikola Tesla in a presentation to the National Electric Light Association.
On 25 March 1925, John Logie Baird was able to demonstrate the transmission of moving pictures at the London department store Selfridges.
Baird’s device relied upon the Nipkow diskand thus became known as the mechanical television. It formed the basis of experimental broadcasts done by the British Broadcasting Corporation beginning 30 September 1929. However, for most of the twentieth century televisions depended upon the cathode ray tube invented by Karl Braun. The first version of such a television to show promise was produced by Philo Farnsworth and demonstrated to his family on 7 September 1927.
Computer networks and the Internet
On 11 September 1940, George Stibitz was able to transmit problems using teletype to his Complex Number Calculator in New York and receive the computed results back at Dartmouth College in New Hampshire. This configuration of a centralized computer or mainframe with remote dumb terminals remained popular throughout the 1950s. However, it was not until the 1960s that researchers started to investigate packet switching — a technology that would allow chunks of data to be sent to different computers without first passing through a centralized mainframe. A four-node network emerged on 5 December 1969; this network would become ARPANET, which by 1981 would consist of 213 nodes.
ARPANET’s development centered on the Request for Comment process and on 7 April 1969, RFC 1 was published. This process is important because ARPANET would eventually merge with other networks to form the Internet and many of the protocols the Internet relies upon today were specified through the Request for Comment process. In September 1981, RFC 791 introduced the Internet Protocol v4 (IPv4) and RFC 793 introduced the Transmission Control Protocol (TCP) — thus creating the TCP/IP protocol that much of the Internet relies upon today.
However, not all important developments were made through the Request for Comment process. Two popular link protocols for local area networks (LANs) also appeared in the 1970s. A patent for the token ring protocol was filed by Olof Soderblom on 29 October 1974 and a paper on the Ethernet protocol was published by Robert Metcalfe and David Boggs in the July 1976 issue of Communications of the ACM.
In telecommunication, a communications system is a collection of individual communications networks, transmission systems, relay stations, tributary stations, and data terminal equipment (DTE) usually capable of interconnection and interoperation to form an integrated whole. The components of a communications system serve a common purpose, are technically compatible, use common procedures, respond to controls, and operate in unison.
Basic elements
A basic telecommunication system consists of three elements:
- A transmitter that takes information and converts it to a signal.
- A transmission medium that carries the signal.
- A receiver that receives the signal and converts it back into usable information.
For example, in a radio broadcast the broadcast tower is the transmitter, free space is the transmission medium and the radio is the receiver. Often telecommunication systems are two-way with a single device acting as both a transmitter and receiver or transceiver. For example, a mobile phone is a transceiver.
Analogue or digital
Signals can be either analogue or digital. In an analogue signal, the signal is varied continuously with respect to the information. In a digital signal, the information is encoded as a set of discrete values (for example ones and zeros). During transmission the information contained in analogue signals will be degraded by noise. Conversely, unless the noise exceeds a certain threshold, the information contained in digital signals will remain intact. Noise resistance represents a key advantage of digital signals over analogue signals.
Networks
A network is a collection of transmitters, receivers and transceivers that communicate with each other. Digital networks consist of one or more routers that work together to transmit information to the correct user. An analogue network consists of one or more switches that establish a connection between two or more users. For both types of network, repeaters may be necessary to amplify or recreate the signal when it is being transmitted over long distances. This is to combat attenuation that can render the signal indistinguishable from noise.
Channels
A channel is a division in a transmission medium so that it can be used to send multiple streams of information. For example, a radio station may broadcast at 96.1 MHz while another radio station may broadcast at 94.5 MHz. In this case, the medium has been divided by frequency and each channel has received a separate frequency to broadcast on. Alternatively, one could allocate each channel a recurring segment of time over which to broadcast—this is known as time-division multiplexing and is used in optic fiber communication.
Modulation
The shaping of a signal to convey information is known as modulation. Modulation can be used to represent a digital message as an analogue waveform. This is known as keying and several keying techniques exist (these include phase-shift keying, frequency-shift keying and amplitude-shift keying). Bluetooth, for example, uses phase-shift keying to exchange information between devices.
Modulation can also be used to transmit the information of analogue signals at higher frequencies. This is helpful because low-frequency analogue signals cannot be effectively transmitted over free space. Hence the information from a low-frequency analogue signal must be superimposed on a higher-frequency signal (known as the carrier wave) before transmission. There are several different modulation schemes available to achieve this (two of the most basic being amplitude modulation and frequency modulation). An example of this process is a DJ’s voice being superimposed on a 96 MHz carrier wave using frequency modulation (the voice would then be received on a radio as the channel “96 FM”)
Basic block diagram of a communication system
The System is composed of the following functional Blocks:
The Transmitter
Transmitter includes encoding, compression and error correcting operations, modulation process if some type of carrier to be used.
The Channel
Where this refers to the available media like transmission lines, fiber cables, the radio frequency spectrum over which the information coming from a transmitter actually propagates or travels to a particular receiver.
The Receiver
Where the receiver performs the processes: decoding, decompressing, comparing error correction codes, demodulating the radio signal to separate it from any carrier that was used.
The Noise
The noise is generally normal in communication process. We cannot prevent it but we can minimize it. When you say noise this is unwanted form of a signal that disturbs, interferes and affects the wanted signal in the communication process.
Transmitter
A transmitter is an electronic device which, usually with the aid of an antenna, propagates an electromagnetic signal such as radio, television, or other telecommunications.
Types
Generally in communication and information processing, a transmitter is any object (source) which sends information to an observer (receiver). In radio electronics and broadcasting, a transmitter usually has a power supply, an oscillator, a modulator, and amplifiers for audio frequency (AF) and radio frequency (RF). Sometimes a device (for example, a cell phone) contains both a transmitter and a radio receiver, with the combined unit referred to as a transceiver.
In consumer electronics, a common device is a Personal FM transmitter, a very low power transmitter generally designed to take a simple audio source like an iPod, CD player, etc. and transmit it a few feet to a standard FM radio receiver.
In industrial process control, a “transmitter” is any device which converts measurements from a sensor into a signal, conditions it, to be received, usually sent via wires, by some display or control device located a distance away. Typically in process control applications the “transmitter” will output an analog 4-20 mA current loop or digital protocol to represent a measured variable within a range.
Block diagram of a simple transmitter
1 = Audio stage
2= modulator
3= Oscillator
4= RF power amplifier
Description
| Item | Name | Description |
| 1 | Audio Stage | · Amplifies (increases) the weak signal coming from the microphone. |
| 2 | Modulator | · The audio (or data) signal is modulated onto the radio frequency carrier in this modulator stage.
· Modulation can be by varying the amplitude (or height) of the carrier known as amplitude modulation (am) or by slightly changing its frequency waveform known as Frequency Modulation (FM). |
| 3 | Frequency Generator or Oscillator | · The Frequency generation stages (often known as the oscillator) define the frequency on which the transmitter will operate.
· Incorrect setting of these stages can easily result in operation outside of the amateur band, and hence interference to other (non-amateur) radio users. · The Foundation License only permits the use of commercially available equipment or commercial kits built strictly in accordance with the instructions. · The Foundation License does NOT permit you to design and build your own transmitters. |
| 4 | RF Power Amplifier | · The power amplification of the radio signal is carried out in the final stage of the block diagram. It makes the signal stronger so that it can be transmitted into the aerial.
· The RF power amplifier output must be connected to a correctly matched antenna (the “Load”) to work properly. Use of the wrong antenna, or no antenna, can result in damage to the transmitter. |
A practical FM transmitter
The circuit given below is a two transistor FM transmitter circuit.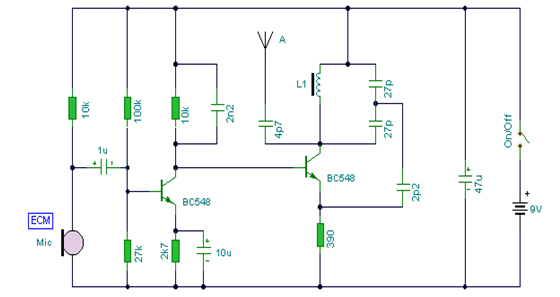
Figure: Two transistor FM transmitter
Receiver
A receiver is an electronic circuit that receives its input from an antenna, uses electronic filters to separate a wanted radio signal from all other signals picked up by this antenna, amplifies it to a level suitable for further processing, and finally converts through demodulation and decoding the signal into a form usable for the consumer, such as sound, pictures, digital data, measurement values, navigational positions, etc.
Types
Various types of radio receivers may include:
- Consumer audio and high fidelity audio receivers and AV receivers used by home stereo listeners and audio and home theatre system enthusiasts.
- Communications receivers, used as a component of a radio communication link, characterized by high stability and reliability of performance.
- Simple crystal radio receivers (also known as a crystal set) which operate using the power received from radio waves.
- Satellite television receivers, used to receive television programming from communication satellites in geosynchronous orbit.
- Specialized-use receivers such as telemetry receivers that allow the remote measurement and reporting of information.
- Measuring receivers (also: measurement receivers) are calibrated laboratory-grade devices that are used to measure the signal strength of broadcasting stations, the electromagnetic interference radiation emitted by electrical products, as well as to calibrate RF attenuators and signal generators.
- Scanners are specialized receivers that can automatically scan two or more discrete frequencies, stopping when they find a signal on one of them and then continuing to scan other frequencies when the initial transmission ceases. They are mainly used for monitoring VHF and UHF radio systems.
- Internet radio device
Block diagram of a simple receiver
11 1= Tuning and RF amplifier
2= Detection
3= Audio amplifier
4= Loud speaker
Description
| Item | Name | Description |
| 1 | Tuning and RF amplifier | · Tuning selects just the signal we want to hear from all the many different radio signals being transmitted on different radio frequencies.
· Tuning uses tuned circuits consisting of inductors (coils of wire) and capacitors. · The RF amplifier increases the signal received from the air by the antenna. · Antenna is connected to receivers by special wires known as feeders. |
| 2 | Detection | · Detection is the process of recovering the original modulating signal.
· The process is sometimes known as de-modulation (reverse of modulation in the transmitter). |
| 3 | Audio Amplifier | · The audio amplifier increases the detected audio signal to level that can be used with a loudspeaker. |
| 4 | Loudspeaker | · Sometimes headphones are used in place of the loudspeaker. |
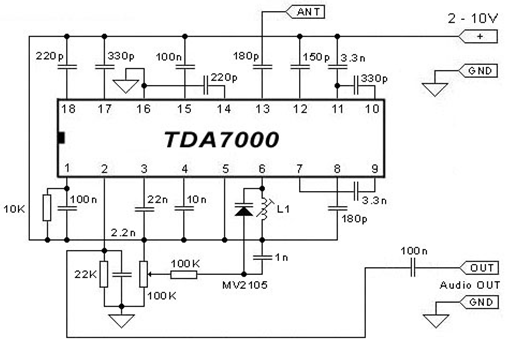
A practical FM receiver
Figurefigure: TDA7000 FM receiver
Modulation
The process of superposing low frequency audio signals on waves with high frequency is called modulation. Here, the low frequency signal is called the modulating signal and the high frequency wave, since it carries the information, is called a carrier wave. The resultant wave due to their superposition is called a modulated wave.
Generally, the carrier wave is a sine wave, which is mathematically represented as:
C (t) = Ac cos(2πfct)
Where,
Ac= amplitude of the carrier wave
fc = carrier frequency
Necessity of modulation
(1) For effective transmission of high frequency waves, antenna length is small and hence such an antenna can be easily constructed.
(2) The study of electromagnetic radiation indicates that the transmitted power by an antenna of a given length is inversely proportional to the wavelength X. This point shows that an antenna can transmit short wavelength radiation with more efficiency. Hence for this purpose also, the use of high frequency (short wavelength) waves is inevitable.
(3) If there is more than one transmitter in a region and if these transmit their respective information simply using frequency of audio signals, then all such signals get mixed. Normally, it is not possible to separate information of one transmitter from the information of other transmitters. Such a situation can be avoided if every transmitter is assigned different high frequencies for information transmission.
The conclusion of the present discussion is that if the transmission is done using high frequency instead of low frequency, then difficulties do not arise. Hence, the modulation process becomes necessary.
Types of modulation
There are mainly two types modulation.
1.Analoge modulation
2.Digital modulation
Types of analoge modulation
1. Amplitude modulation(AM)
2. Frequency modulation(FM)
3. Phase modulation(PM)
Types of digital modulation
1. Amplitude shift keying(ASK)
2. Frequency shift keying(FSK)
3. Phase shift keying(PSK)
4. Pulse code modulation(PCM)
Amplitude Modulation
In Amplitude Modulation the instantaneous value of the carrier amplitude changes in accordance with the amplitude and frequency variations of the modulating signal.
For example, changes in the signal strength can be used to reflect the sounds to be reproduced by a speaker, or to specify the light intensity of television pixels. It was also the original method used for audio radio transmissions, and remains in use today by many forms of communication—”AM” is often used to refer to the medium wave broadcast band .
Figure: Amplitude Modulation
Frequency Modulation
In FM, the carrier amplitude remains constant, while the carrier frequency is changed by the modulated signal. As the amplitude of the information signal varies, the carrier frequency shift in proportion. As the modulating signal amplitude increases, the carrier frequency increases. If the amplitude of the modulating signal decreases the carrier frequency decreases. 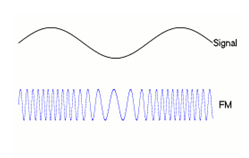 Figure: 2.7 Frequency Modulation
Figure: 2.7 Frequency Modulation
Amplitude shift keying
Amplitude-shift keying (ASK) is a form of modulation that represents digital data as variations in the amplitude of a carrier wave.
The amplitude of an analog carrier signal varies in accordance with the bit stream (modulating signal), keeping frequency and phase constant. The level of amplitude can be used to represent binary logic 0s and 1s. We can think of a carrier signal as an ON or OFF switch. In the modulated signal, logic 0 is represented by the absence of a carrier, thus giving OFF/ON keying operation and hence the name given.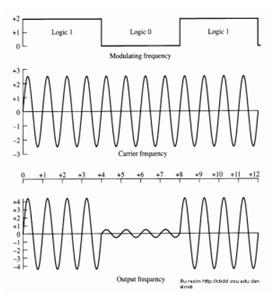
Figure: Amplitude shift keying
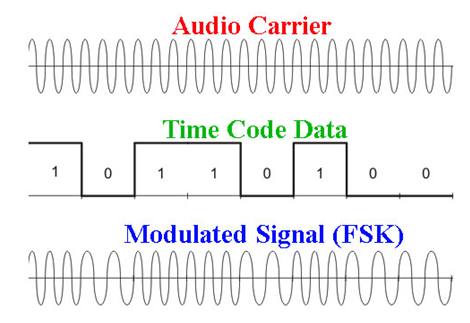
Frequency shift keying
Frequency-shift keying (FSK) is a frequency modulation scheme in which digital information is transmitted through discrete frequency changes of a carrier wave. The simplest FSK is binary FSK (BFSK). BFSK literally implies using a pair of discrete frequencies to transmit binary (0s and 1s) information. With this scheme, the “1” is called the mark frequency and the “0” is called the space frequency. The time domain of an FSK modulated carrier is illustrated in the figures to the right.
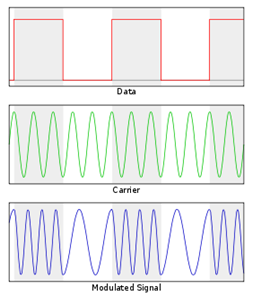 Figure: Frequency-shift keying (FSK)
Figure: Frequency-shift keying (FSK)
PIC16F84A Microcontroller
Microcontroller Introduction
A microcontroller (sometimes abbreviated µC, uC or MCU) is a small computer on a single integrated circuit containing a processor core, memory, and programmable input/output peripherals. Program memory in the form of NOR flash or OTP ROM is also often included on chip, as well as a typically small amount of RAM. Microcontrollers are designed for embedded applications, in contrast to the microprocessors used in personal computers or other general purpose applications.
Microcontrollers are used in automatically controlled products and devices, such as automobile engine control systems, implantable medical devices, remote controls, office machines, appliances, power tools, and toys. By reducing the size and cost compared to a design that uses a separate microprocessor, memory, and input/output devices, microcontrollers make it economical to digitally control even more devices and processes. Mixed signal microcontrollers are common, integrating analog components needed to control non-digital electronic systems.
A micro-controller is a single integrated circuit, commonly with the following features:
- central processing unit – ranging from small and simple 4-bit processors to complex 32- or 64-bit processors
- discrete input and output bits, allowing control or detection of the logic state of an individual package pin
- serial input/output such as serial ports (UARTs)
- other serial communications interfaces like I²C, Serial Peripheral Interface and Controller Area Network for system interconnect
- peripherals such as timers, event counters, PWM generators, and watchdog
- volatile memory (RAM) for data storage
- ROM, EPROM, EEPROM or Flash memory for program and operating parameter storage
- clock generator – often an oscillator for a quartz timing crystal, resonator or RC circuit
- many include analog-to-digital converters
- in-circuit programming and debugging support
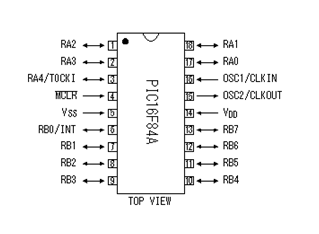
PIC16F84A
| This powerful (200 nanosecond instruction execution) yet easy-to-program (only 35 single word instructions) CMOS Flash/EEPROM-based 8-bit microcontroller packs Microchip’s powerful PIC® architecture into an 18-pin package. Easily adapted for automotive, industrial,
appliances low power remote sensors, electronic locks and security applications.
Some features of PIC16f84a are given below.
|
|||||||||||||||||||||
|
Pin configuration
Theoretical Representation:
In this project our main objective is to investigate different kind of modulation, demodulation, transmitter and receiver. Here we choose FSK transmitter and receiver, because it can operate with binary bits. FSK is a digital version of Frequency modulation so the basic concepts of FSK remain same as FM.
Frequency Modulation
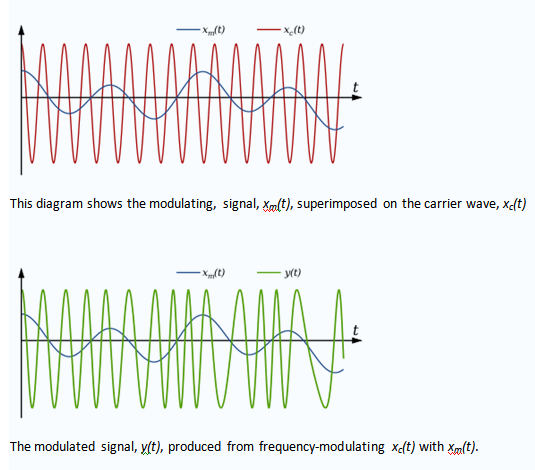
In telecommunications, frequency modulation (FM) conveys information over a carrier wave by varying its frequency. In analog applications, the difference between the instantaneous and the base frequency of the carrier is directly proportional to the instantaneous value of the input signal.
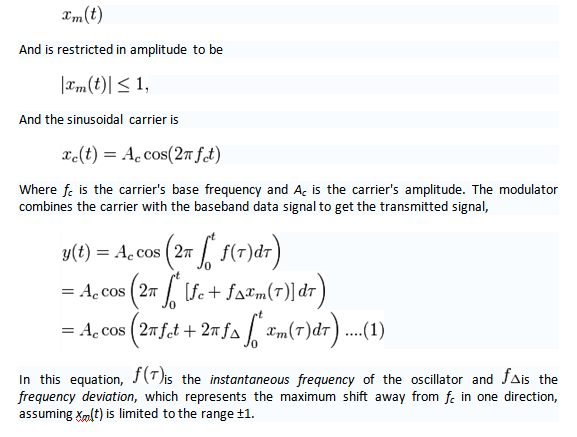
Suppose the baseband data signal (the message) to be transmitted is
Whilst it is an over-simplification, modulating signals are usually represented as a sinusoidal Continuous Wave signal with a frequency fm. The integral of such a signal is
Thus, in this specific case, equation (1) above simplifies to:
Where the amplitude of the modulating sinusoid, is represented by the peak deviation .
The harmonic distribution of a sine wave carrier modulated by such a sinusoidal signal can be represented with Bessel functions – this provides a basis for a mathematical understanding of frequency modulation in the frequency domain.
Modulation index
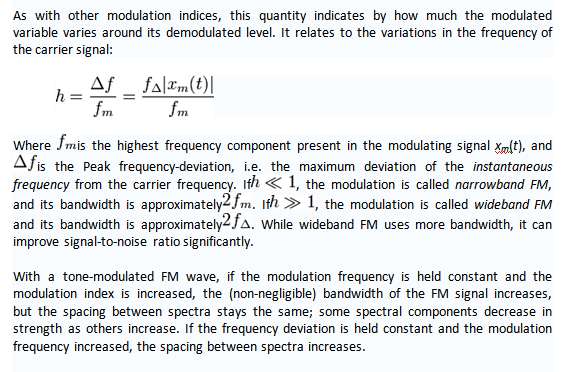
As with other modulation indices, this quantity indicates by how much the modulated variable varies around its demodulated level. It relates to the variations in the frequency of the carrier signal:
Where is the highest frequency component present in the modulating signal xm(t), and is the Peak frequency-deviation, i.e. the maximum deviation of the instantaneous frequency from the carrier frequency. If, the modulation is called narrowband FM, and its bandwidth is approximately. If, the modulation is called wideband FM and its bandwidth is approximately. While wideband FM uses more bandwidth, it can improve signal-to-noise ratio significantly.
With a tone-modulated FM wave, if the modulation frequency is held constant and the modulation index is increased, the (non-negligible) bandwidth of the FM signal increases, but the spacing between spectra stays the same; some spectral components decrease in strength as others increase. If the frequency deviation is held constant and the modulation frequency increased, the spacing between spectra increases.
Carson’s rule
A rule of thumb, Carson’s rule states that nearly all (~98%) of the power of a frequency-modulated signal lies within a bandwidth of
Where, as defined above, is the peak deviation of the instantaneous frequency from the center carrier frequency?
Implementation
FM signals can be generated using either direct or indirect frequency modulation.
- Direct FM modulation can be achieved by directly feeding the message into the input of a VCO.
- For indirect FM modulation, the message signal is integrated to generate a phase modulated signal. This is used to modulate a crystal controlled oscillator, and the result is passed through a frequency multiplier to give an FM signal
A common method for recovering the information signal is through a Foster-Seeley discriminator.
Applications
Broadcasting
FM is commonly used at VHF radio frequencies for high-fidelity broadcasts of music and speech (see FM broadcasting). Normal (analog) TV sound is also broadcast using FM. A narrow band form is used for voice communications in commercial and amateur radio settings. The type of FM used in broadcast is generally called wide-FM, or W-FM. In two-way radio, narrowband narrow-fm (N-FM) is used to conserve bandwidth. In addition, it is used to send signals into space.
As the name implies, wideband FM (W-FM) requires a wider signal bandwidth than amplitude modulation by an equivalent modulating signal, but this also makes the signal more robust against noise and interference. Frequency modulation is also more robust against simple signal amplitude fading phenomena. As a result, FM was chosen as the modulation standard for high frequency, high fidelity radio transmission: hence the term “FM radio” (although for many years the BBC called it “VHF radio”, because commercial FM broadcasting uses a well-known part of the VHF band; in certain countries, expressions referencing the more familiar wavelength notion are still used in place of the more abstract modulation technique name).
FM receivers employ a special detector for FM signals and exhibit a phenomenon called capture effect, where the tuner is able to clearly receive the stronger of two stations being broadcast on the same frequency.
A high-efficiency radio-frequency switching amplifier can be used to transmit FM signals (and other constant-amplitude signals). For a given signal strength (measured at the receiver antenna), switching amplifiers use less battery power and typically cost less than a linear amplifier. This gives FM another advantage over other modulation schemes that require linear amplifiers, such as AM and QAM
Frequency shift keying
In digital transmission repeaters can regenerate digital signals and improve the ability against noise interference, and the use of encoding techniques can provide debugging and correction functions. But digital signals often occur distortions due to high frequency components are easily attenuated for a long distance transmission. To improve the disadvantage, a particular processing (modulation) is need for this purpose. Frequency shift keying (FSK) is a type of FM in which the modulating signal shifts the output between two predetermined frequencies – usually termed the mark and space frequencies.
FSK technique is widely used for the transmission of Teletype information. FSK standards have involved for the years. For radio Teletype, the frequency of 2124Hz represents mark or 1, and 2975 Hz represents space or 0.
For data transmission over telephone and landlines, the commonly used frequencies are:
Space = 1270Hz
Mark = 1070Hz
And
Space = 2225Hz
Mark = 2025Hz
The frequency difference of FSK signals 200Hz.
Figure No: Frequency shift keying (FSK)
FSK Modulator:
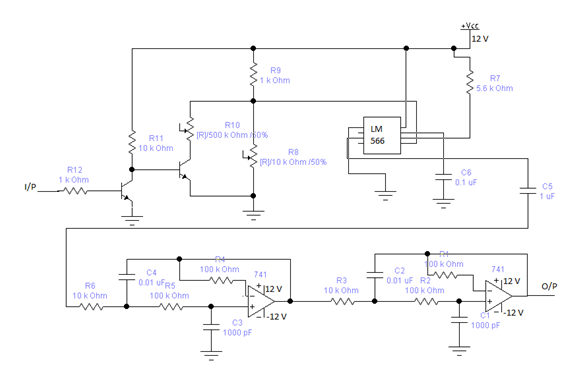
The FSK modulator is used to convert the digital signals (square wave) into the analog signal having two different frequencies corresponding to the input levels. In this experiment, we use the frequencies of 1070Hz 1270Hz represent space and, respectively. A voltage controlled oscillator (VCO) can easily generate these two frequencies. A practical FSK modulator using the LM566 VCO is shown in Fig.3.2.In such cases, the oscillating frequency of LM566 can be found by
fo =2 (Vcc-Vin) / R7 C6 Vcc
Where Vcc is the power voltage applied to LM566 pin 8, and Vin is the VCO control voltage applied to pin 5.
If Vcc is constant, proper value of R7, C6 and Vin are determined to generate the LM566 output frequencies f0 of 1072Hz and 1272Hz. In practice, the limitations of using Lm566 VCO are as follows;
2kΩ≤ R7≤20kΩ
0.75≤Vin ≤Vcc
f0≤500kHz
10V≤Vcc≤24V
To generate the frequencies of 1070Hz and 1270Hz exactly, the digitals input levels, such as TTL levels 0V and 5V must be converted to proper voltage levels before applying to the input of VCO. The levels shifter (Q1 and Q2) provides this purpose. The Q1 acts as a NOT gate. In other words, when Q1 input is high (5V), then Q1 conducts and the output goes to low (about 0.5V) causing the Q2 to cutoff. If Q1 input is low (0V), the Q1 is off and its output rises to high (5V), and thus the Q2 conducts. When the Q2 is OFF, the input voltage of VCO is given by:
V1 = R8 Vcc / (R8 + R6)
And the output frequency of VCO is f1, when Q2 conducts, the input voltage of VCO is
V2 = (R10 // R8) Vcc /(R10 // R8) + R9
And the output frequency is f2. Therefore the output frequencies f1 ₌ 1270Hz and f2 =1070Hz can be obtained by carefully adjusting the R10 and R7 values, both U1 and U3 are the second order low pass filters. The four order low pass filter formed by cascading these filter is used to filter the frequency harmonics components on the output of LM566 and therefore the FSK modulated signals obtained.
If the FSK modulated signals mentioned above is desired to transmit by an antenna, a mixer is required to modulate signal to the frequency range in RF band.
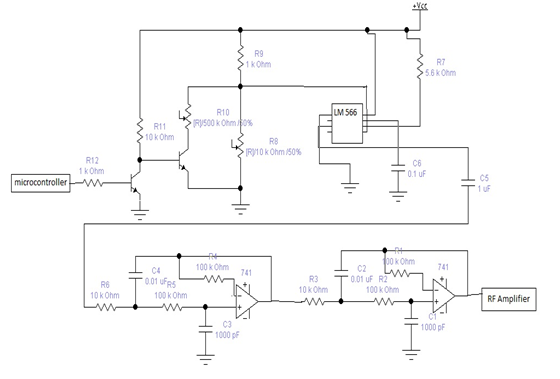
Figure: 3.4 FSk Transmitter
The above figure shows a Frequency Shift Keying transmitter. Here we use a Microchip manufactured Pic16f84a microcontroller to generate the message signal. Basically we program the microcontroller such a way so that it can generate the ASCCI value of character ‘a’. Then we input this into the modulator.
After the FSK modulation, the modulated signal is inputted into a RF amplifier module. The RF amplifier module contains a tuning circuit and an antenna.
The output signal of the tuning circuit is in our desired frequency. Then the signal is transmitted through the antenna.
FSK demodulator
Phase locked loop (PLL)
The digital signal is converted into the FSK signal by the FSK modulator for long distance communications. At receiver section, an FSK modulator is necessary to recover the original digital signal from the received FSK signal. A phase locked loop (PLL) is a good choice for this purpose. In short, the phase locked loop is the control system that tracks the frequency and phase of the input signal. Recently, the PLL is widely used as a demodulator in many types of analog communication systems. Such as the AM demodulator, FM demodulator, frequency selector and Chroma subcarrier acquisition in color TV receiver. Similarly, many digital PLL have been developed to track a carrier or bit synchronizing signal in digital communication systems.
Basically, a PLL includes three major sections:
Phase detector (PD)
Loop filter (LF)
Voltage controlled oscillator (VCO)
Consider the PLL block diagram shown in figure 3.4. If Vin change frequency, an instantaneous change will result in a phase change between A and B and hence a dc level change at the output. This level shift will change the frequency of the VCO to maintain lock. If the PLL is used as an FSK demodulator and the FSK signal is applied to the input the output V1 and V2 will correspond to the input frequencies f1 and f2, respectively. Thus an input frequency change has converted into an output dc level change. When the PLL output is connected to the input of voltage comparator having a reference between V1and V2, the output signal of the comparator is the digital signal, or the FSK demodulated signal.
Block diagram of PLL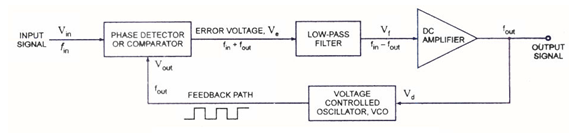 Figure: Phase lock loop
Figure: Phase lock loop
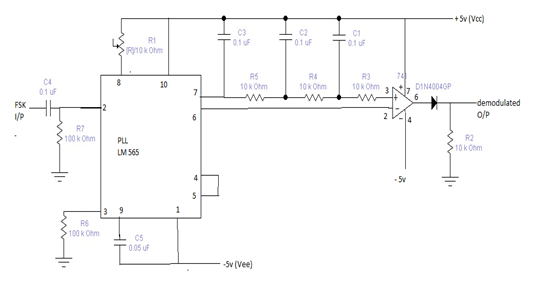
FSK demodulator circuit
Figure: FSK demodulator circuit
In the demodulator we use LM565 PLL to perform an FSK demodulator shown in figure 3.5. The LM565 PLL including the phase detector, VCO and amplifier operates below the frequency of 500 kHz. The phase detector operates as a double balanced modulator and the VCO is an integrator-Schmitt circuit. Power supplies +5V and -5V are applied to Vcc (pin 10) and Vee (pin 1), respectively. The FSK signal is applied to the input of the phase detector. Since a frequency multiplier is needless in our project, pin 4 and pin 5 are directly tied together. The reference output (pin6) provides the reference voltage of the comparator U2. The combination of internal resistor Rx and external capacitor C3 operates as the loop filter. The timing components R1 and C5 determine the free running frequency of the VCO. In designing with the LM565, the important parameters of interest are as follows:
Free running frequency
In the absence of the input signal, the output frequency of the VCO is called the free running frequency f0. In the circuit of figure 3.5, the free running frequency of LM565 is determined by the timing components C5 and R1, and can be found by
f0 ~ 1.2 /4R1 C5
Lock range
Initially the PLL is in already locked state and the VCO is running at some frequency. If the input frequency fi is always from the VCO frequency fo, locking may still occur. When the input frequency reaches a specific frequency where the PLL loses lock, the frequency difference of fi and fo is called the lock range of the loop. The lock range of LM565 can be found by
fL = 8f0 / Vc
Capture range
Initially, the loop is unlocked and the VCO is running at some frequency. If the input frequency fi is close to the VCO frequency fo, unlocking may maintain. When the input frequency reaches a specific frequency where the PLL locks, the frequency difference of fi and fo is called the capture range of the loop. The capture range of LM565 can be found by In the circuit of figure 3.6, components R5, R4, R3, C3, C2 and C1 perform the low pass filter to reduce the output ripple. The digital levels of FSK demodulated signal are compatible TTL levels.
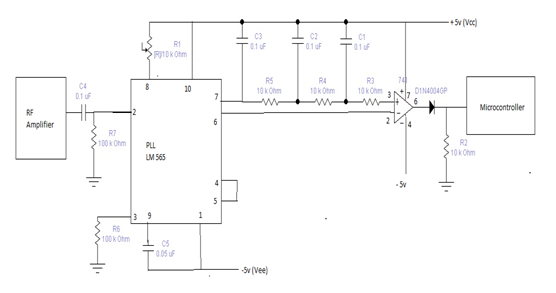
FSK Receiver
Figure: FSK Receiver
The above figure shows a Frequency Shift Keying receiver. At first the signal is input into the RF amplifier module. The RF amplifier contains an antenna, a filter and an amplifier.
After filtering and amplification the signal goes to the FSK demodulator. The demodulator recovers the original message signal Then the demodulated signal arrives into the microcontroller. The microcontroller is programmed such a way so that it can read the demodulated signal and convert it into the ASCII value of ‘a’. Then microcontroller will send this value into the output for display.
Design and Implementation
Tools and components
Modulator
VCO IC LM566
Transistor C 945
Op amp IC 741
Microcontroller PIC 16F84A
Resistors
Capacitors
Breadboard
Oscilloscope
Demodulator
PLL LM565
Op amp 741
Microcontroller PIC 16F84A
Resistors
Capacitors
Breadboard
Oscilloscope
Design and Implementation
Modulator
1 .Arrange all of component needed for the modulated circuit.
2. Connect the circuit properly showed in the figure 3.3.
3. Connect 5V dc to digital signal input using the oscilloscope, observe the LM566 output frequency (pin 3) and adjust R8 variable resistor to obtain the frequency of 1070Hz.
4. Connect digital signal input to ground (0V) using the oscilloscope, observe VLM566 output frequency (pin 3) and adjust R10 variable resister to obtained the frequency of 1270Hz.
5. Save the output signal generator to TTL level and the frequency of 200Hz and then connect it into the digital signal input.
6. Use the oscilloscope to observe FSK output signal.
Demodulator
1. Arrange all of component needed for the modulated circuit.
2. Connect the circuit properly showed in the figure 3.6
3. Observe the free – running frequency of LM565 and adjust R1 to obtain a frequency of 1170Hz.
4. Connect a 1070Hz, 2VP-P sine wave to the input terminal save oscilloscope vertical input to dc range and observe the output wave form.
5. Change the input frequency to 270Hz and repeat step 4.
6. Apply a 200Hz TTL squire wave to input of FSK modulator.
7. Connect the output of FSK modulator to the input of FSK demodulator.
8. Use the oscilloscope to observe the demodulated output wave form.
After testing the modulator and the demodulator we concentrate at the transmitter and the receiver.
Transmitter
1. Write the program of the microcontroller to generate the serial data correspond to the ASCII value of ‘a’.
2. Then we programmed the microcontroller by the programmer.
3. Connect the microcontroller with the modulator circuit.
4. Design a RF radio frequency amplifier to amply the FSK modulated signal and connect the output of the FSK modulator with the input of RF amplifier.
5. Design a tuning circuit to get our desired frequency and connect its input with the output of the RF amplifier.
6. Connect an antenna with the tuning circuit for the transmission.
7. Finally test the transmission.
Receiver
The FSK modulated signal is received by the receiver antenna.
1. Input the received signal into a RF amplifier.
2. Then connect the RF amplifier output into the FSK demodulator. The demodulator will recover the original message signal.
3. Then write a program for the microcontroller to take input from the demodulator and convert it into the ASCII value.
4. Connect the microcontroller with the demodulator.
5. Finally check the microcontroller output is it the ASCII value of ‘a’.
Conclusion:
Discussion:
In this project our main goal is to gather knowledge about communication system, different kind of modulation and made a FSK transmitter and receiver. Here we use two microcontrollers with the transmitter and receiver for generate and display the message signal which is the ASCII value of character ‘a’.
The reason of choosing FSK transmitter and receiver is because, its use for long distance digital communication. It is also used in modems. Another application of FSK is at low and very low frequencies (below 300 kilohertz). At these frequencies, keying speeds are limited by the “flywheel” effect of the extremely large capacitance and inductance of the antenna circuits. These circuits tend to oscillate at their resonant frequencies. Frequency-shifting the transmitter and changing the antenna resonance by the same keying impulses will result in much greater keying speeds. As a result, the use of these expensive channels is much more efficient.
And the main advantage of FSK over CW modulation is it rejects unwanted signal (noise) that are weaker than the desired signal.
Finally we can say that, we complete this project successfully.
Future Work
Our system is one kind of pager. Our future plan is to interface the transmitter with a PC (personal computer) and make our system possible to transmit, receive and display any kind of short message.
References:
Books
Communication electronics
By Louis E. Frenzel
Electronics communication systems
By George Kennedy
Bernard Davis
Principles of electronic circuits
By Dr. Rezaul Karim Mazumder
Websites:
www.google.com
www.en.wikipedia.org
www.tpub.com
www.microchip.com
www.tutornext.com
www.electronics-diy.com